In the world of Information Security, we have all heard of the Center for Internet Security Top 20 Critical Security Controls (CSC's) which is formerly known as the SANS Top 20. This is a list of the 20 IT Security Controls that an organization can implement to strengthen their IT Security position and mitigate their risks of an attack. One of the CSC's that is gaining more and more attention, both in the news and through Regulatory Requirements, is CSC 19: Incident Response and Management.
Most organizations have a Business Continuity Plan and Disaster Recovery Plan which has some element of Cybersecurity built in. However, an Incident Response Plan is a critical component for an organization to create, manage, monitor, and adjust. This plan will identify, within your organization, who is a part of the Incident Response Team and what their roles are on the team. And, just like a Business Continuity Plan, the Incident Response Plan should be tested and updated on a regular basis. But why? Why do we need to have a separate plan focused specifically on IT Security Incidents and why can't we just lump it into our BCP plan? Well, there are several reasons, listed below: 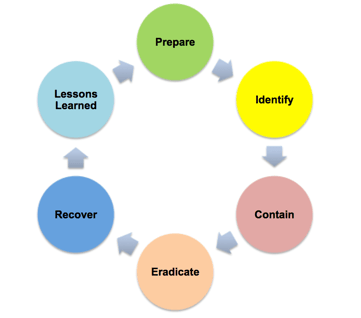
- Regulatory Requirements - Some Regulations specifically outline the need for an Incident Response Plan. For example, in PCI DSS 3.2, this is called out in requirement 12.10. For Healthcare, NIST 800-61 provides specific guidance around creating a plan for handling breaches called the Computer Security Incident Handling Guide
- Best Practice - When a natural disaster occurs, many businesses in that geographic location are affected. When an IT Security Incident occurs, only that targeted organization feels the effect, therefore the response is different. In fact, CSC 19 says the following: "Protect the organization's information, as well as reputation, by developing and implementing an Incident Response infrastructure (e.g. plans, defined roles, training, communications, management oversight) for quickly discovering an attack and then effectively containing the damage, eradicating the attacker's presence, and restoring the integrity of the network and systems."
- Damage Control - When a natural disaster takes place, typically a response from a business is not needed. When a breach occurs, most of the time a response is needed. Who drafts that response? Who delivers that response? Is this done internally or through a PR firm?




No Comments Yet
Let us know what you think