Share this
Previous story
← The NIST Cybersecurity Framework - The Detect Function
Next story
Beware of Hurricane Harvey Phishing Scams →
It has come to our attention that cyber criminals have begun exploiting a vulnerability within Microsoft PowerPoint’s Object Linking and Embedding (OLE) interface to evade antivirus detection in an attempt to silently install malware applications on Windows based computer systems.
This exploit, known as the CVE-2017-0199 vulnerability is a new PowerPoint attack route based on a previously identified and patched vulnerability in Windows systems (CVE-2017-8570 Vulnerability) which would infect a machine through a Rich Text File. Through the use of a malicious PowerPoint attachment, which can fool virus scans due to its plain text infection activation method, a logo document is downloaded as a background process when the PowerPoint is run, calling forth a silent PowerShell script to install the RATMAN.EXE Trojan file. This file is a highly versatile back door remote access tool that opens a Windows system to virtually every malware type and runs without a system shell.
This spear phishing attack is initiated through an email which can be commonly mistaken as a legitimate correspondence. Hackers tend to be impersonating an employee of the organization or one of its partners. It is important to check that the email address and domain of the sender are safe and creditable. These phishing emails take a different approach as they will purport to be from a cable manufacturing provider and will generally target organizations in the electronics manufacturing industry. The sender's address will be disguised to look like a message from a business partner and the email will appear to relate to an order request, with an attachment containing shipping information. The attachment will be a real PowerPoint file, though malignant:
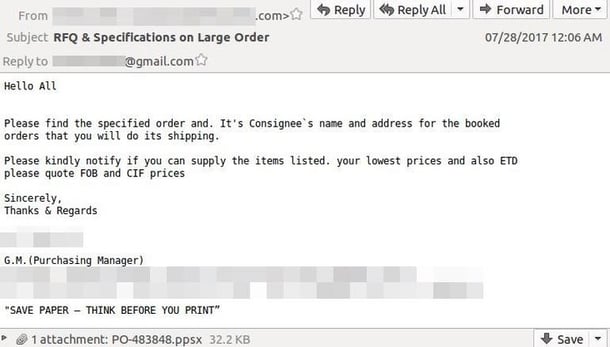
If you believe that this attack has already taken place on a system in your environment, an immediate malware and antivirus scan should be run on the identified system using reliable solutions with the most recent databases such as Sophos Antivirus or Malwarebytes. The system should be temporarily removed from network access as it is possible that this vulnerability allows the installation of applications which can disable antivirus or antimalware or uninstall them completely, depending on the attacker's goal. Network attached systems with shared storage may be used as a gateway to spread ransomware or network based malware through this exploit. Installing the previously distributed patch for the CVE-2017-8570 vulnerability through Windows update should be performed after. Affected systems with infections that disable all system protections, anti-threat applications, and system restore functionality should be considered for a clean Windows refresh to ensure the removal of the exploit and infection.
If you have any questions about this specific vulnerability, please don't hesitate to contact us. If you are looking for assistance or need a good place to start to protect your systems from being compromised, download a copy of our Critical Security Controls eBook to help boost your infosec program!
These Related Stories



No Comments Yet
Let us know what you think