What is Protected Health Information (PHI)?
Protected Health Information (PHI) is a key element in healthcare, governed by stringent legal and ethical standards. This blog explores what PHI encompasses, its significance under HIPAA regulations, and the crucial distinction between PHI and electronic PHI (ePHI). The blog also delves into the various components and exceptions of PHI, underscoring the importance of its protection and responsible management in the healthcare sector.
Protected Health Information (PHI) Defined
What does PHI stand for? PHI stands for Protected Health Information, which covers a range of personal health details that are carefully protected by specific legal provisions. So, what exactly falls under PHI? Essentially it includes any information in records that can potentially identify an individual. This goes beyond just what is in a doctor’s office as it also includes things like diagnoses, treatments, billing, and insurance details.
Understanding PHI extends beyond recognizing its components. It involves acknowledging the importance of securely managing and responsibly sharing this data. In the United States the Health Insurance Portability and Accountability Act (HIPAA) plays a major role in this aspect. HIPAA establishes guidelines to safeguard information and ensures that it is not revealed without explicit consent from the patient. The legislation serves as the cornerstone of data security within the healthcare industry. The range of information classified as PHI is extensive. Includes identifiers such as names and birth dates as well as more specific details like Social Security Numbers and unique biometric data such as fingerprints.
In the healthcare field, it is important to understand that any piece of medical or payment history becomes PHI when associated with personal identifiers. This medical PHI definition and PHI data meaning is vital not only for healthcare professionals but also for patients themselves. It emphasizes the significance of comprehending the utilization and protection of information. Safeguarding PHI goes beyond simply following regulations; it represents the values of trust and confidentiality in healthcare highlighting the essentiality of treating personal health information with utmost caution and honesty.
What is ePHI?
So, we have answered, “What is PHI in healthcare?” but what about ePHI? We have established that any data that can identify a patient is categorized as Protected Health Information (PHI). Now let us imagine this information exists in a digital format, such as an electronic medical record. This is referred to as electronic PHI, or ePHI for short. HIPAA, which safeguards patient privacy, emphasizes security measures for all PHI. However, when it comes to ePHI there is an emphasis due to its susceptibility to copying and sharing. Because of this, ePHI often necessitates additional robust safeguards to prevent any digital disasters. Protecting the patient’s information is always the top priority, whether the information is on paper or in pixels.
The 18 HIPAA Identifiers
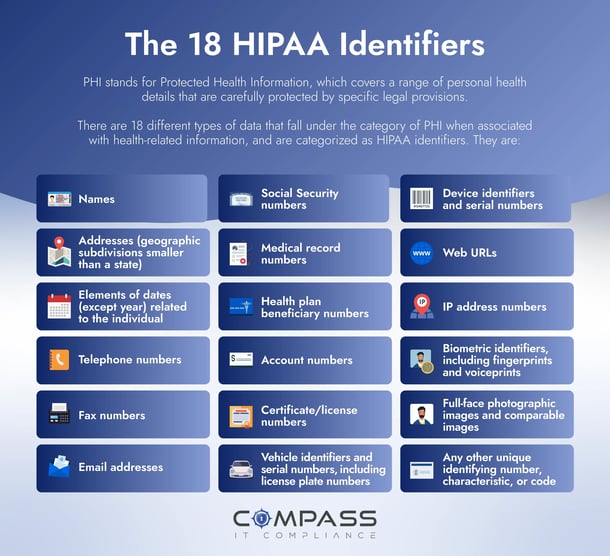
Examples of PHI include a patient's name, address, or banking details that can be employed to identify or even impersonate someone, potentially for illicit activities. Should these diverse types of protected health information fall into the wrong hands, it poses a significant risk, leaving patients exposed to nefarious activities. These specific details, such as names and addresses, are categorized as HIPAA identifiers. There are 18 different types of data that fall under the category of PHI when associated with health-related information. Those types of data include:
- Names
- Geographic subdivisions smaller than a state
- Elements of dates (except year) related to the individual
- Telephone numbers
- Fax numbers
- Email addresses
- Social Security numbers
- Medical record numbers
- Health plan beneficiary numbers
- Account numbers
- Certificate/license numbers
- Vehicle identifiers and serial numbers, including license plate numbers
- Device identifiers and serial numbers
- Web URLs
- IP address numbers
- Biometric identifiers, including fingerprints and voiceprints
- Full-face photographic images and comparable images
- Any other unique identifying number, characteristic, or code
What Is Not PHI?
To comprehend the concept of healthcare privacy within the context of the Health Insurance Portability and Accountability Act (HIPAA), it is essential to have knowledge about both what is considered protected health information and what is not considered protected health information. HIPAA includes exceptions for types of information that are not categorized as PHI, which aids in defining the limits of privacy laws.
One significant exception is de-identified health data. When personal identifiers such as names, addresses, Social Security numbers and other identifying information are removed from health data, it no longer falls under the category of PHI. Therefore, datasets without these identifiers are not counted as PHI.
Another area where HIPAA does not apply is regarding health information found in employment records. This includes records related to leave disability claims or workers compensation that form a part of an individual’s employment history; HIPAA does not cover these.
Additionally, certain educational records protected by the Family Educational Rights and Privacy Act (FERPA) do not fall under the scope of PHI. This includes health records that schools might have, like immunization records. Understanding what is and is not PHI under HIPAA is key to navigating the intersection of health, privacy, and the law.
Why Does PHI Matter?
Understanding the critical importance of safeguarding Protected Health Information (PHI) in healthcare is a must. It is about more than just keeping records secure; it is about protecting our most personal and sensitive information. Imagine if someone got their hands on your medical history or even just your basic details like age or address. The risks of identity theft and privacy breaches are real and frightening. PHI is not just about our past illnesses; it is the full picture of who we are.
Consider your most recent doctor's visit. The personalized advice and treatment you received were thanks to the complete access your healthcare provider had to your health records. Without this full picture, the risk of incorrect treatments or harmful interactions increases significantly.
But there is another side to this. If a clinic or hospital slips up and PHI gets out, it is not just a matter of a slap on the wrist. We are talking serious financial hits from fines and legal battles. And let us not forget the trust factor. Once a patient loses trust in their healthcare provider, it is tough to win back. Their reputation can take a real beating.
At the end of the day, it is about peace of mind. When we seek medical help, we should not have to worry about who is peeking at our records. We need to know our data is handled with care and respect. That is why protecting PHI is not just ticking a box for legal compliance; it is a promise to keep our health information safe and secure, a cornerstone of trust in our healthcare system.
De-identification of Protected Health Information
De-identification is a crucial process in the world of health information privacy. It involves removing or altering data that might reveal someone's identity. This transformation is key for preserving privacy, as it ensures information cannot be traced back to an individual. This is especially relevant under the Privacy Rule, which dictates how Protected Health Information (PHI) is managed.
When it comes to using PHI in research, the Privacy Rule generally requires specific, written consent from individuals. However, there are exceptions. In certain circumstances, PHI can be used without consent, like when an Institutional Review Board (IRB) or Privacy Board waives the need for Authorization, or in cases involving limited data sets, preparatory research, or information about deceased individuals.
The moment PHI is de-identified correctly, it escapes the constraints of HIPAA regulations, allowing for broader sharing in research contexts. The Privacy Rule outlines two key methods for achieving this de-identification, balancing the need for privacy with the benefits of research. The first method involves statistical verification to ensure that the data cannot be linked back to specific individuals. The second approach involves removing the 18 specific identifier elements that have the potential to reveal someone's identity, their family members, employers, or people they live with.
By adhering to these de-identification standards, covered entities can balance the need for research with the imperative of protecting individual privacy.
PHI Disposal Considerations
One aspect of compliance that is often overlooked but holds utmost importance is the proper disposal of Protected Health Information (PHI). Why is this aspect so crucial? It ensures the preservation of privacy and security even when the information is no longer required. Improper disposal of PHI can result in improper access leading to identity theft, fraud, and other severe privacy concerns. That is why understanding how to dispose of PHI goes beyond mere rule following – it plays a vital role in ethical patient care. The following aspects must be considered regarding the proper disposal of PHI.
Developing and Documenting PHI Disposal Policies
For Covered Entities, Business Associates, and their Subcontractors, it is vital to have clear policies for disposing of both PHI and electronic PHI (ePHI). These policies need to be well-documented and form an integral part of the organization's Security Policies and Procedures. This ensures that sensitive information is handled and disposed of correctly, maintaining compliance and safeguarding patient privacy. This documentation acts as a roadmap and a compliance record.
Understanding Media Types and Retention Periods
Organizations should evaluate the distinct types of media where PHI is stored, such as paper documents or various forms of electronic media like hard drives and flash drives. Each type may require different disposal methods. Additionally, it is important to align the retention period for PHI records with HIPAA's mandated six years while considering any state regulations that might extend this period.
What Methods Are Acceptable for Destruction of Protected Health Information?
Determining acceptable methods for destroying protected health information (PHI) is vital in maintaining security. Organizations must carefully select methods that ensure complete destruction without compromising patient confidentiality or violating any regulations.
Safe Storage Pre-Destruction
Identifying and maintaining a secure location for storing media before its destruction is another key aspect. This could involve specific bins or areas designated for items awaiting shredding or pickup.
Employee Training on PHI Disposal
Under HIPAA regulations, workforce members who are involved in or oversee the disposal of PHI must be adequately trained. This training should cover the specific procedures for disposal and the handling of media during the interim period before destruction.
Sticking to these guidelines is about more than just avoiding fines or legal issues. At its core, the focus is on establishing trust and prioritizing confidentiality in client interactions. If Protected Health Information (PHI) is mishandled it can lead to consequences for patients and significantly damage an organization’s reputation. It is essential to dispose of PHI according to regulations to respect patient privacy and protect data effectively. This practice does not just keep your organization legally safe; it also strengthens the trust your patients have in your care and services.
PHI Compliance Best Practices
In today's healthcare field, our role goes much deeper than just following the rules. Gaining patients' trust and keeping healthcare system honest hinges greatly on how we treat Protected Health Information (PHI). Healthcare professionals must wholeheartedly commit to the guidelines for safeguarding PHI. These are not just rules; they are a comprehensive set of practices that range from handling physical paperwork to managing digital data. The following section explores key best practices that are vital for protecting PHI from unauthorized access and misuse. Implementing custom healthcare software solutions can further bolster these practices, ensuring a higher level of security and efficiency in managing PHI. It is about more than compliance; it is about ensuring patients' confidentiality and maintaining their trust in the healthcare services.
Physical Environment Considerations:
- Create designated areas for reviewing and handling PHI that are not easily accessible or visible to unauthorized personnel. This includes securing areas where written materials and charts containing PHI are used.
- Strategically locate printers, copiers, and fax machines in areas that minimize the risk of public viewing of PHI. Promptly retrieve printed documents containing PHI.
- Implement the use of computer privacy screens and screen savers to minimize the risk of unauthorized viewing of PHI on monitors. If privacy screens are not feasible, position monitors to reduce visibility from public areas.
- Avoid leaving PHI materials in common areas like conference rooms, desks, or counters, where they might be accessed by individuals without a need-to-know.
- When escorting patients, delivery personnel, or other visitors in areas where PHI is accessible, take necessary precautions to prevent their viewing of confidential information.
Conversations Involving PHI:
- Be continuously aware of the surrounding environment when discussing PHI to prevent accidental disclosure. This includes being mindful of who might overhear the conversation.
- Keep discussions about PHI to the minimum necessary information required for the intended purpose, especially in semi-public areas like shared offices.
- Utilize private spaces, such as separate rooms, for discussions involving PHI with colleagues, patients, and family members, ensuring confidentiality.
PHI Storage and Accessibility:
- Securely store documents containing PHI in locked cabinets or rooms, particularly when they are not in active use or after working hours.
- Establish stringent physical and procedural controls to limit access to PHI, such as key or combination locks, and authorize access levels to ensure only those who require the information can access it.
- Manage the keys to locked files and areas diligently, avoiding leaving them in locks or in places where unauthorized persons might find them.
Electronic PHI Security:
- Establish stringent access controls to PHI stored on computer workstations and databases, ensuring only authorized personnel can access the information.
- Adhere to a strict protocol of logging out or securing workstations containing PHI whenever they are left unattended to prevent unauthorized access.
- Regularly update passwords and install security patches as directed by the IT department to enhance cybersecurity measures.
- Develop protocols for the deletion or erasure of PHI from electronic storage devices once the information is no longer needed, while following guidelines for hardware disposal to ensure residual data is not accessible.
Faxing and Emailing PHI:
- Limit the use of faxing for transmitting PHI, reserving it for situations where other communication methods are impractical. Ensure that the content of faxes is limited to the minimum necessary PHI.
- Pre-program frequently used fax numbers to reduce errors and regularly confirm their accuracy. Implement a protocol for fax cover sheets that includes a confidentiality notice and sender/recipient details.
- When emailing PHI, use secure, encrypted email systems approved by IT. Limit the PHI shared in emails to the minimum necessary and obtain prior consent for emailing PHI to patients or third parties.
Compass Makes HIPAA Compliance Easy
Protecting Protected Health Information (PHI) and staying in line with HIPAA regulations is a tricky task for any organization. That is where Compass IT Compliance comes into play. Our team, deeply versed in the nuances of HIPAA, commits to top-tier data security standards. We offer customized solutions to help your organization tackle the intricacies of PHI protection. Our experts guide you in setting up strong security measures, crafting effective data protection plans, and ensuring that your PHI management aligns with regulatory demands.
But we do more than just help you comply. Compass IT Compliance is all about embedding a security-first mindset within your organization. We provide training for your staff, conduct thorough audits, and support you in maintaining a secure environment for sensitive health information. Choosing to work with us means not just ticking off compliance boxes; it means building a foundation of trust with your patients and clients.
In a time when data breaches are a constant threat, partnering with Compass IT Compliance offers the confidence that your PHI, whether handled manually or through EVV software, is in capable hands. Reach out to us to learn more and discuss how we can address your specific needs. Let us ensure your PHI security together.
Contact Us
Share this
You May Also Like
These Related Stories

Understanding the Difference Between HIPAA & HITRUST

What Are the 3 Important Rules for HIPAA Compliance?

.webp?width=2169&height=526&name=Compass%20white%20blue%20transparent%202%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)
.webp?width=610&height=362&name=March%202024%20CTA%20(8).webp)
No Comments Yet
Let us know what you think