Is Your Head in the Cloud? Traditional Security vs. Cloud Security
When someone asks you if your head is in the clouds, there is an implication of being impractical. However, in a cloud-based environment, or in those organizations that conduct part or all of their operations in the cloud, the question has quite the opposite meaning. Although cloud computing is not a new concept, its adoption has exploded over the past several years. Businesses have many advantages for moving to cloud environments, such as flexible capacity and scalability, increased responsiveness, improved availability and business continuity, faster time to deployment, and cost savings. However, like traditional security as we once knew it, cloud security comes with its own set of risks. Whether you use a private or public cloud, hackers will continue to use arcane methods to access organizations’ sensitive and confidential data.
In the recent Flexera 2021 State of the Cloud Report, statistics showed that 92% of enterprises have a multi-cloud strategy and 80% have a hybrid cloud strategy. Many organizations today across all industry verticals are using, on average, eight cloud services from multiple vendors. The following graph depicts a forecast of the number of clouds in a multi-cloud environment from 2020 to 2023 by industry:
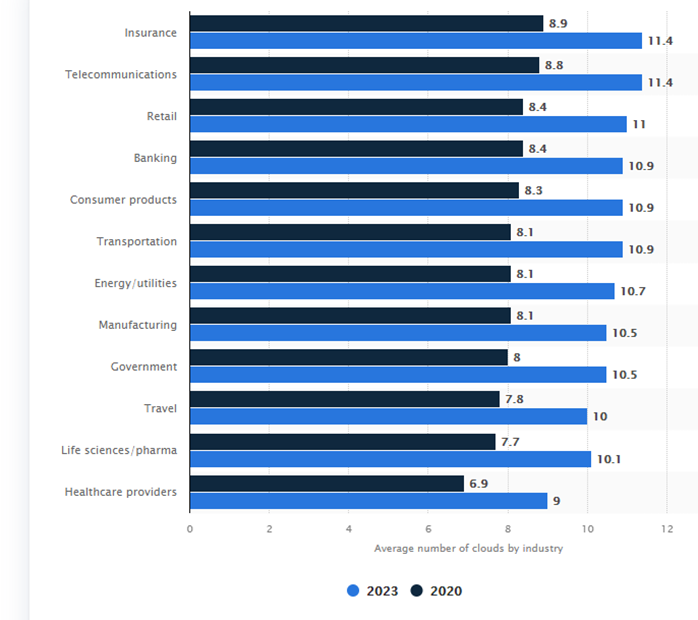
Source: https://www.statista.com/statistics/1209623/multi-cloud-usage-global-industry/
Traditional Security versus Cloud Security
Security has rapidly moved from companies’ four walls to a much broader scope outside of those walls. Corporate perimeters are dissolving and becoming more blurred. On-premises infrastructures are always more prone to errors and mistakes that vigilant cyber attackers can exploit. Conversely, cloud-based infrastructure is very different from an on-premises data center, and traditional security tools and strategies are not always able to secure it effectively. As more organizations adopt digital transformation, cloud computing is becoming the norm for collecting, storing, and managing data. The increased expansiveness of the cloud also increases an organization's potential attack surface, allowing for more opportunistic attacks. To further complicate the matter, traditional security controls often do not satisfy cloud security needs or requirements.
The cloud is no more or less secure than on-premises security because people on both sides can make mistakes and compromise security. The more pressing question becomes, “Which of these options provides the better options to protect and reduce risk to organizational assets?”
Traditional security controls are not adequate to mitigate and protect against the new threats in cloud environments. However, besides the foundational principles, the same security concerns affect both on-premises and cloud-based systems: unauthorized data exposure and leaks, weak access controls, susceptibility to attacks, and availability disruptions. Security threats are constantly evolving, and cyber criminals are becoming more advanced. In fact, with more and more data being stored in the cloud, attackers have turned their attention to the cloud.
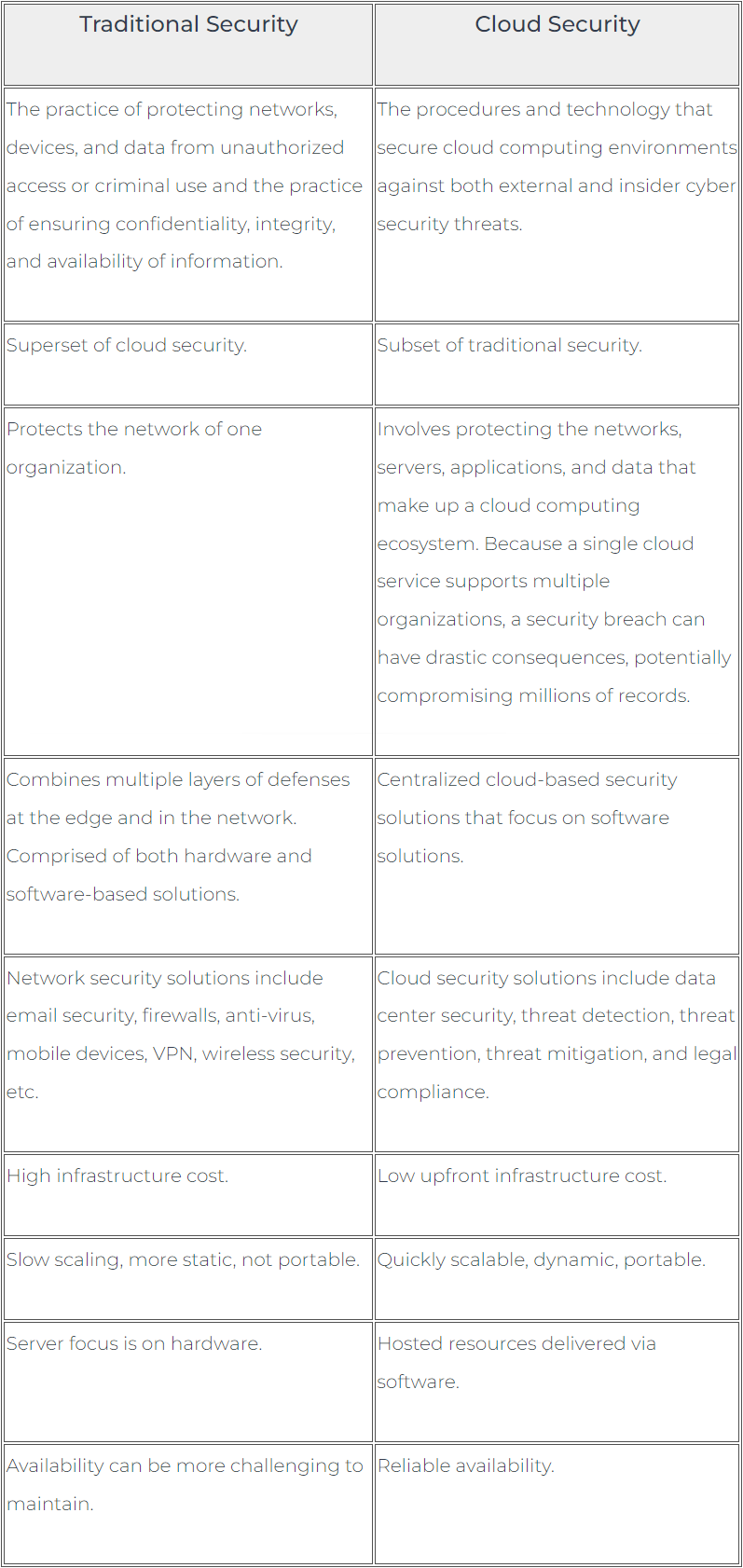
The following table summarizes the differences between traditional (cyber) security and cloud security:
Cloud Security – Who is Responsible?
All the major promises of the cloud come with one major challenge: security. More often than not, organizations place their trust in cloud providers to ensure a secure environment. However, cloud providers do not always know the risk associated with a customer's systems and data because there is no visibility into other components in the customer's environment and the security requirements of those components. Failing to take ownership of cloud security is a serious downfall that could lead organizations to suffer data loss, system breaches, and devastating attacks.
While cloud providers offer increasingly robust security measures as part of their cloud services, the customer is ultimately responsible for securing their workloads in the cloud. Many small or medium businesses (SMBs) tend to think that security responsibilities are shifted to the cloud service provider (CSP). An important point to underscore is that while adopting cloud platforms is about outsourcing computing infrastructure, you cannot outsource data security. However, no matter what type of cloud infrastructure an organization chooses, both the organization and CSP have responsibilities regarding security controls. Responsibilities can be the sole responsibility of the cloud customer, the CSP, or both, hence the term shared responsibility.
It is vital to define responsibilities for securing different aspects of cloud computing to understand the risk that cloud security threats pose. The split of responsibilities among the public cloud provider and the customer organization varies greatly depending on the computing model: Software as a Service (SaaS), Platform as a Service (PaaS), or Infrastructure as a Service (IaaS).
The following graph differentiates between the cloud customer and CSP responsibilities and where responsibilities are shared:
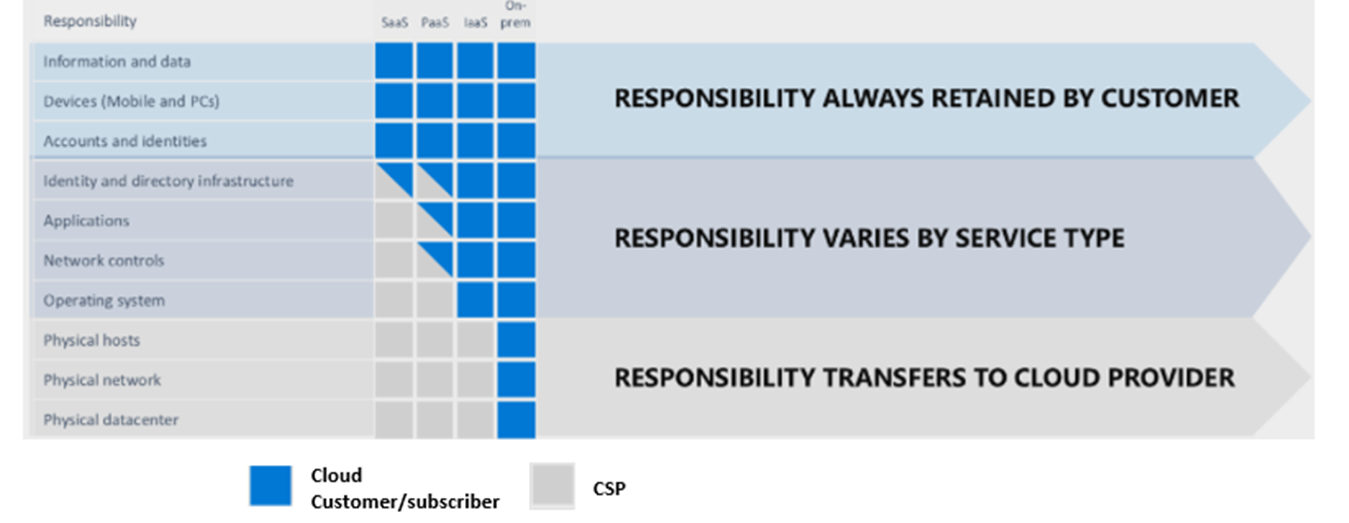
Image Source : https://www.tenable.com/blog/cloud-security-3-things-infosec-leaders-need-to-know-about-the-shared-responsibility-model
Cloud Security Risks and How to Mitigate
As with traditional security threats, cloud security threats are constantly evolving. However, as more organizations continue to move data and applications to the cloud, there are some common security threats organizations should be aware of when using cloud services. Although not an exhaustive list and not in any particular order, the following provides some of the more common threat and risk mitigation techniques to consider:
|
Threat |
Risk |
Mitigations |
|
Access Management / Unauthorized Access |
A majority of cloud security threats, and cybersecurity threats in general, can be linked to identity and access management (IAM) issues. IAM challenges are intensified by cloud use of the monitoring and managing of the sheer number of cloud accounts needed as well as challenges with defining roles and privileges. The absence of multifactor authentication (MFA) or improperly configured security or compromised credentials can enable an attacker to gain direct access, potentially without an organization’s knowledge.
|
|
|
Data Breach, Leaks, and Loss |
The immense amount of data stored by CSPs in public and private clouds has become a gold mine for hackers. Because of the flow of large volumes of data among employees and cloud systems, it becomes vulnerable to interceptions by hackers on the move. The confidential information leaks can then be subject to sale in the black market for money or used for ransom. Because cloud-based systems are available via the internet, they have some inherent security risks. Although hackers' motivations may vary, they often search for data that was not meant for public consumption to use for their gain. This may include personal health information (PHI), personally identifiable information (PII), trade secrets, politically valuable information, financial information, and intellectual property. Enterprises lose data in the cloud for many different reasons. Sometimes, it results from a data breach where a threat actor has accessed a system to steal data. However, some more innocuous reasons may also be at work. Accidental deletion by a CSP may occur. If data is encrypted and the customer loses the encryption key, they could lose the data forever. Natural disasters such as fires, hurricanes, or earthquakes could also be to blame. No matter the reason, permanently losing data can be disastrous for the company. |
|
|
DDoS Attacks |
Cloud-based data is prone to denial-of-service attacks (DDoS) that prevent users from accessing the resources by overloading the workflow. Although they rarely result in data breaches, they can cause intolerable stoppage or bring all operations to a standstill. They can be performed by one actor (denial-of-service) or many actors (distributed denial-of-service) to interrupt the service in a virtualized cloud environment by using up all its CPU, RAM, disk space, or network bandwidth. This action can have long-ranging impacts on a business, causing a loss of customers, diminished organizational reputation, or halting business operations. |
|
|
Insecure APIs |
Application programming interfaces (API) are often the front door to cloud services, making it an obvious entry point for attackers. The API may be the only asset with an IP address that is publicly available, making it the most exposed. Organizations may need to relinquish API credentials to third parties, subjecting them to further discovery, thus creating new cloud security challenges. |
|
|
Insider Threats |
Insiders reside within the organization, such as employees, independent contractors, interns, and other staff. A malicious insider may deliberately exceed or abuse their access privileges that adversely affects the organization’s data. Cloud-based services provide increasing access levels for insiders, especially those that rely solely on CSPs for security. In some cases, the threat may be caused by unintentional human error, such as accidentally uploading sensitive or private information to a public repository. Organizations also need to be aware of “Shadow IT” whereby people install or use cloud services without getting IT authorization, increasing risk to the entity. |
|
|
Malware |
Malware has become a standard tool of choice for hackers. First, they gain access via an email or social media link. Then, once inside, additional malware is downloaded, encoded to bypass detection, and installed directly. Successful malware attacks enable the attacker to steal data and compromise the integrity of sensitive information.
|
|
|
Misconfigurations |
When assets are set up incorrectly, they are vulnerable to attack. Cloud misconfigurations often include insecure storage, excessive permissions, the use of default credentials, and ineffective change control.
|
|
Final Thoughts
Cybercrime is a business, and cybercriminals select their targets based upon the expected profitability of their attacks, of which many attacks have become more opportunistic. Many factors contribute to these types of attacks because cloud-based environments are directly accessible from the public internet, are often improperly secured, and contain sensitive and valuable data. Moreover, because many different companies use the cloud, a successful attack is more likely to be repeated several times with a high probability of success.
Organizations should ensure the development of a risk management plan for their cloud security framework. At a high level, these steps involve:
- Identifying where your sensitive / confidential data is stored, processed, or transmitted
- Determining the data security needs
- Developing a plan for access control, identifying and documenting who has access to which systems and data
- Communicating data security preferences to your cloud providers. Most will work with you to select the appropriate controls for your company’s needs
- Developing a vendor management program
- Developing incident response and disaster recovery plans in case your data is compromised
As always, the Compass IT Compliance team is on standby to answer any questions you may have regarding cloud security. Our experience dates back to the inception of cloud solutions, and you are welcome to submit a contact us form with any questions you have for myself or a member of our team!
Contact Us
Share this
You May Also Like
These Related Stories

Enhancing Cloud Security Posture Management (CSPM)

Securing Your Cloud Environment – Who is Responsible?

.webp?width=2169&height=526&name=Compass%20white%20blue%20transparent%202%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)
No Comments Yet
Let us know what you think