Cyber & Physical Security: Why You Need Both
Cybersecurity attracts an enormous amount of attention due to cyberattacks that are publicized daily. As more devices are connected to the Internet, they become attractive targets for criminals; therefore, the attack surface increases exponentially. The adoption and integration of Internet of Things (IoT) and Industrial Internet of Things (IIoT) devices has led to an increasingly interconnected mesh of cyber-physical systems (CPS), which expands the attack surface and obscures the once clear functions of cybersecurity and physical security.
As with any technological advancement, connected devices have become a common target for cyber criminals hoping to steal valuable data or even cause potential destruction of property. Connectivity comes at a cost, and protecting connected devices through effective cybersecurity now goes hand-in-hand with physical security, creating a convergence of the physical and digital domains that reflects the increasingly interconnected state of the world in which we function.
No matter what industry vertical an organization operates within, it is important to understand why cybersecurity is needed to support physical security. It should come as little surprise to those in the security industry that devices ranging from doorbells to artificial hearts to surveillance cameras can be targeted by cyber criminals. It is no longer strictly a technology concern, but people, processes, and technology are all at risk if proper precautions are not implemented.
Cyber vs. Physical Security
In today’s security landscape, very few businesses are running without CPS in place. However, as IoT technology evolves and more systems move into the cloud, companies need to re-examine their strategies constantly. Traditionally, physical security measures such as access control, security personnel, and surveillance were treated as standalone functions, with little regard for how data and IT systems are innately linked to physical security. When applications and systems are increasingly mobile or cloud-based, it is almost impossible to achieve compliance for sensitive data and identity protection without an integrated physical and cybersecurity strategy. Systems and devices can provide threat actors with additional attack vectors to connect to networks, infect other devices, and exfiltrate data. Today, organizations must consider physical security as a primary pillar of cybersecurity.
Examples of incidents involving cyber and physical can be categorized three ways:
| Cyberattack on physical systems |
In March of 2021, more than 150,000 cloud-based Verkada physical security cameras were hacked. This incident provided the hackers with access to thousands of cameras through a broad cross-section of industries, from hospitals, schools, and corporate offices to police stations and jails. Not only were the hackers able to see into a variety of facilities, but they also accessed certain private data. For example, they saved video footage taken from the home of a Verkada employee of inmates in detention facilities. They had insight into who used access cards to enter certain hospital rooms. The hackers gained access to Verkada via a username and password for an administrator account that was publicly exposed on the Internet. |
| Physical systems used in cyberattacks | Mirai was one of the most infamous botnet attacks in 2016 and was the first significant botnet to infect insecure IoT devices. The Mirai botnet resulted in a massive, distributed denial of service (DDoS) attack that left much of the Internet inaccessible on the east coast of the United States. |
| Physical security of cyber systems | On April 21, 2017, Lifespan Corporation filed a breach report with OCR regarding the theft of a laptop when an employee’s car was broken into. The laptop was unencrypted and contained electronic protected health information, including patients’ names, medical record numbers, demographic data, and medication information. The laptop was never recovered. |
CPS Convergence
Cyber-Physical Systems (CPS) are collections of physical and computer components that are integrated to operate a process safely and efficiently. CPS systems have been integrated into critical infrastructures (smart grid, industry, supply chain, healthcare, military, agriculture, etc.), making them an attractive target for security attacks for various purposes, including economic, criminal, military, espionage, political, and terrorism. Thus, any CPS vulnerability can be targeted to conduct dangerous attacks against such systems. Cyber and physical assets represent a significant amount of risk to physical security and cybersecurity – each can be targeted, separately or simultaneously, to result in compromised systems and/or infrastructure. Different security aspects can be targeted, including confidentiality, integrity, and availability. To enable the broad adoption and deployment of CPS systems and to leverage their benefits, it is essential to secure these systems from any possible attack, internal or/and external, passive or active.
A cyber and physical security convergence strategy uses measures to restrict access to certain spaces, along with cybersecurity practices to secure the connected network and limit access to sensitive data. Physical and IT security convergence addresses the interconnected nature of these components and treats them as one rather than as separate business entities. A successful cyber or physical attack on connected industrial control systems (ICS) and networks can disrupt operations or deny critical services to society. For example:
- A security gap in access controls, such as unauthorized access to facilities or system permissions, can allow an individual to use a universal serial bus (USB) device or other removable hardware to introduce a virus or malware into a network.
- Heating, ventilation, and air conditioning (HVAC) systems can be virtually overridden, causing a rise in temperature that renders network servers inoperable.
- A cyberattack on telecommunications can impair communication with law enforcement and emergency services, resulting in delayed response times.
- A cyberattack exploiting healthcare vulnerabilities can compromise sensitive data or cause a connected medical device to malfunction, resulting in injury or loss of life.
If an adversary has physical access to a space or network, all information systems and data are considered “fair game” and are vulnerable to compromise and theft. Systems and devices may be left behind and unattended outside the view of security cameras; screens may still be unlocked with access to files, network shares, and other resources; and sensitive or confidential data may still be open in plain view on the screen and can be captured, stolen, modified, and/or deleted. Any exfiltrated information on the screen or in paper form regarding calendar schedules and plans, operational details, personal information, contact lists, details from presentations, etc. could be used in phishing, impersonation, and other cyberattacks used to spread disinformation to incite future conflict.
The CPS architecture consists of three main layers: perception, transmission, and application. Elsevier Public Health Emergency Collection published an article titled “Cyber-Physical Systems Security: Limitations, Issues, and Future Trends” that provides a detailed description of the three layers. The following graphic was referenced in Elsevier’s article and provides a high-level overview of the three CPS layers, including the objective, threat, target, and security measures applicable to each layer:
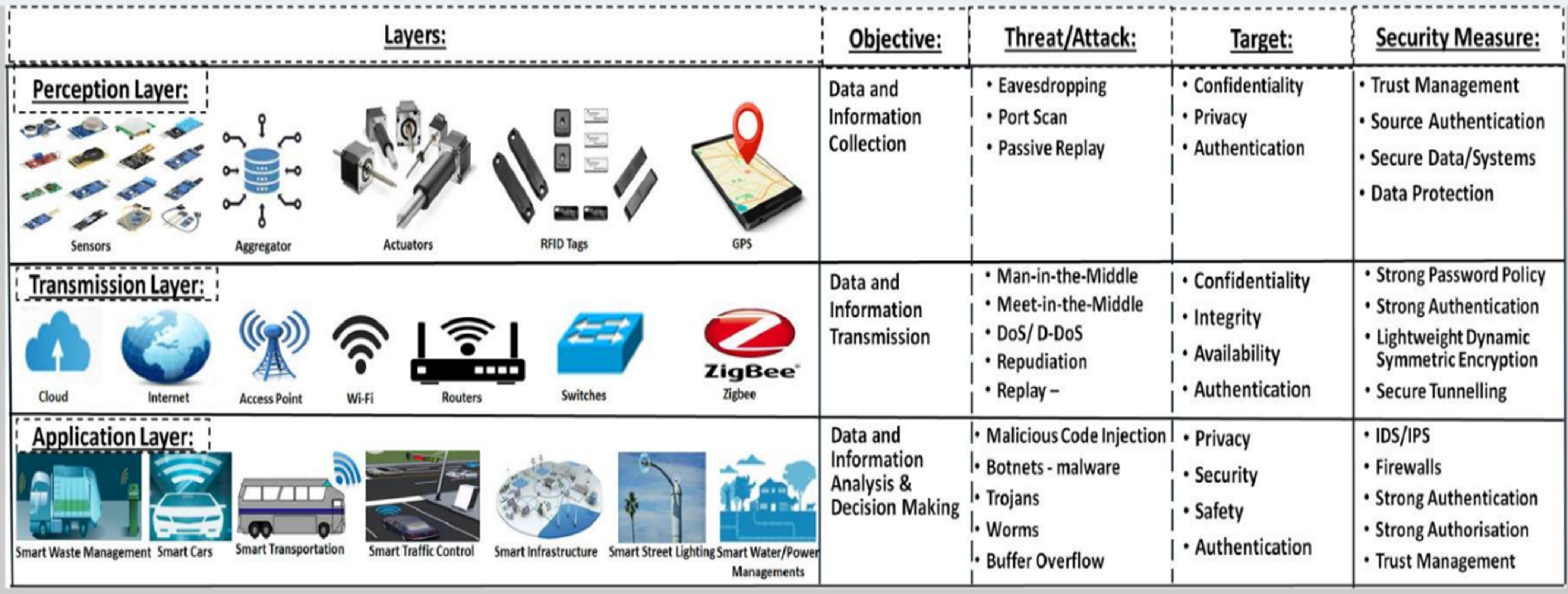
Image source: https://www.ncbi.nlm.nih.gov/pmc/articles/PMC7340599/
While physical security measures are important for preventing unwanted access, a physical and cybersecurity convergence strategy should also cover network devices, applications, and software that power smart, cloud-based devices and security systems as well as the people who manage, monitor, and make business decisions for these functions.
Whether you are responsible for your organization’s physical security or cybersecurity, you still need to apply the same principles:
- Identify and classify your assets and resources (what to protect)
- Identify likely vulnerabilities that threats may exploit (the likelihood)
- Identify plausible threats (who to protect it from)
- Identify the expected cost if bad things happen (the consequences)
The Benefits of Integration
There are many benefits of cyber-physical security convergence:
Cost Savings:
By opening the lines of communication between your facilities team and information security team, you are more likely to identify instances where one team has a mitigating control in place that eliminates the need for the other team to invest in implementing a different control. Additionally, the two groups can collaborate to prevent unexpected costs with a new security investment project.
Incident Response:
When an incident occurs, you are more likely to have a quicker and more effective response if the two teams work in conjunction with one another. Streamlined alerts and effective incident response are only obtainable once your physical security measures and cybersecurity measures are entirely in sync.
Risk Reduction:
With data related to a cyber risk flowing to your facilities team, you are in a better position to take the appropriate steps to manage that risk from a physical perspective and vice versa.
Cybersecurity Helps Build a Physical Security Framework:
Cybersecurity supports the development of a framework for any physical security measures the organization decides to implement. In many ways, the type of cybersecurity measures that a company seeks to implement will determine which kind of physical security barriers and deterrents should be utilized. However, cybersecurity systems have their limitations, which is why physical security should still exist to pick up the slack and further strengthen business security.
Achieving Convergence
There are many steps enterprise security leaders can take to achieve convergence. Here are a few items to consider:
- You cannot provide good cybersecurity without good building security, or if both the cybersecurity and physical security teams continue to be siloed.
- Working together with your IT department improves your organization’s cybersecurity.
- Building a better relationship with your IT group helps you become breach-ready.
- There’s a lot to consider when handling risks: threats, scalability, reputational risks, disaster response, data privacy, etc.
Security should not be important to only one level of the organization - it needs to be important to everyone. Bringing conversations to a level that everyone can understand is critical for everyone to buy in and understand what is expected of them. Incorporating all members of an organization into conversations about security can assist in the understanding of how to approach cybersecurity and physical security to benefit the organization.
Summary
Even though physical and cybersecurity are inherently connected, many organizations still treat these security functions as separate systems. In the past, this was justified because the technology to integrate physical and cybersecurity was not yet available. However, now the problem comes down to governance, making it a priority to create a single body for security policies and bringing physical security and cybersecurity teams together to build strength in your organization. An integrated security architecture offers a foundation for connecting the physical and cyber worlds through intelligence sharing, visibility, control, and automation. As we use more technology in our daily lives, the more there is a need for CPS to help protect your organization from accidental and potentially malicious misuse of these systems and resources and help ensure their intended missions are not disrupted or compromised.
Contact Us
Share this
You May Also Like
These Related Stories

Dictionary Attacks: What They Are and How to Avoid Them

Cybersecurity for Law Firms: Where Is Your Firm At Risk?

.webp?width=2169&height=526&name=Compass%20white%20blue%20transparent%202%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)
Comments (1)