Microsoft Teams – The New Phishing Platform for Hackers?
Many organizations are moving to cloud services for email, voice, and collaboration software. One of the major services being offered is Microsoft Teams. Teams is powerful collaboration software that allows users to share files, screen share, instant message, schedule meetings and voice chat. As far as security goes, Microsoft touts Teams as being one of its most secure services. Microsoft has a compliance framework that highlights the global, regional and industry standards that Teams conforms to. Here is a list of some of those standards:
- FedRAMP
- IRS 1075
- FFIEC
- HITRUST CSF Assurance Program Assessment
- CSA STAR Self-Assessment
- Australia IRAP
- FISC (Japan)
- Commitments included in Tiers A-C
The Microsoft 365 Compliance Framework can be found here.
So, on the surface Teams seems like it’s secure. However, I worry about the social engineering angle. Can Teams be used to conduct social engineering attacks? Based on some initial findings I would have to say yes. What are those initial findings? Well, let’s look at some of the default settings for Teams.
By default, all organizations are setup with external access. This means that users in other companies can find, call, chat and setup meetings with any other Teams users that have not locked down access. I can initiate a chat with almost anyone on the M365 platform. I can also search for email addresses. The fear is that end users might not understand that an outside user can message them from an external Teams chat. We have beaten end users up about email phishing, but have we ever covered chat phishing? To highlight the danger here, I created a trial E5 M365 account called compass12.onmicrosoft.com. It took me 15 minutes to create this trial account. I created three accounts on this M365 instance; myself and the two managing partners of Compass IT Compliance.
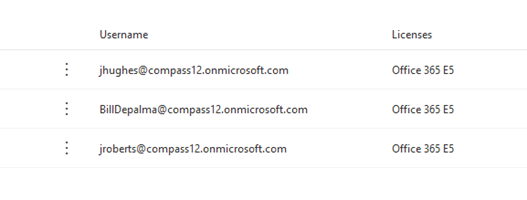
The next step was to play the waiting game to make sure the new domain was fully converged with the rest of the M365 hosted services. So, I waited a day and planned out my attack. I logged in as Jerry Hughes and uploaded a publicly available photo of him.

Now rememeber I am logged in to my fake tennant posing as fake Jerry. I decided to target my team member Peter. I know Peter pretty well and he is extremely loyal to this company. So I came up with a scenario that he would most likely fall for. Here is a screenshot of the message I sent him as the fake Jerry Hughes.
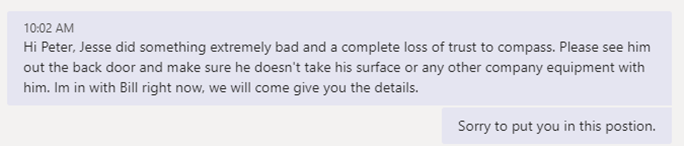
My office is within earshot of where Peter sits. I hear him say out loud, “What?!!” in surprise. Sure enough, a minute later Peter calls for me to come check something out. He then says, “Hey let’s talk outside” and he opens the door out. I then say to him, “What the heck Pete, shows how loyal you are to me!”. I then tell him that I sent the message and see an immediate sigh of relief on my friend’s face. I asked him to show me the message on his computer and on his cell.
Message from Teams client on computer:
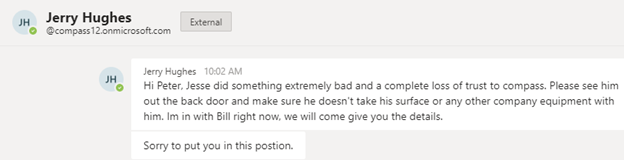
Let’s analyze the above message. There are two tells that this isn’t from Compass IT Compliance’s Jerry Hughes, most notably the “External” tag. The other is the domain name. In this case the profile picture I used didn’t appear, but in other tests where I gave Teams a bit more time to sync, users did see the profile picture too, furthering the illusion, especially if the photo I selected also happens to be the one that Jerry currently uses on his real account. But for a minute let’s reflect on what we know about human behavior. This is something Peter actually taught me from lessons he learned from The Human Hacking Conference he recently attended. Peter immediately saw the name Jerry Hughes and disregarded the two flags that highlighted this message as from an external source because Jerry is an authoritative figure in our company.
The other thing that threw Peter off was the green check mark saying online next to his name and the initial box said JH. To the untrained eye, external can mean perhaps that the user sending the message is on a cell phone. It’s easy to see how an end user could believe this message. Let’s look at how the message looks from a cell phone.
Message from Teams client on cell phone:
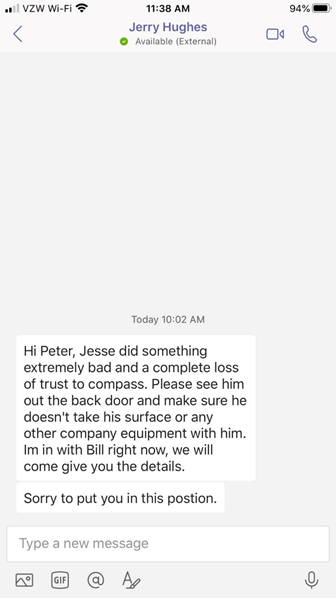
Let’s analyze the message above. The only flag that this is external when viewing from a mobile device is the “External” near the fake Jerry Hughes display name. Notice how small this text is. Again, this is easy to overlook given certain conditions.
I tried another couple of attacks on other co-workers and had similar results. The point is that the industry (in my opinion) is not prepared for this type of social engineering attack. Microsoft should set the default setting to block external Teams messages on this feature.
In conclusion, the Microsoft Teams platform is extremely useful tool that many businesses have adopted to add to the business process. However, default setup of Teams leaves users wide open to a new type of phishing attack. Here are some things you can do to protect your organization:
- Review the use of Teams as an external communication tool. If sending and receiving from external organizations is a must then review Microsoft guidance on only allowing whitelisted domains
- Train your users on Teams usage
- Block external communication to and from Teams
Contact Us
Share this
You May Also Like
These Related Stories
.jpg)
A True Story and Yet Another Cyberattack Victim
QR Code Package Scam: What You Need to Know
.jpg)
.webp?width=2169&height=526&name=Compass%20white%20blue%20transparent%202%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)
No Comments Yet
Let us know what you think