Password Complexity – Going Beyond the Minimum Requirements
As the frequency and scale of cyberattacks has risen sharply over the past decade, we as end users have been repeatedly asked (and often required) to increase the complexity of our passwords. Back when the internet was in its infancy, the idea of creating a complex and tough-to-guess password might have been encouraged to avoid a malicious actor guessing your password via a lucky guess, a commonly used word like “123456”, or some public information such as your last name. But as time went on and technology advanced, these bad actors began utilizing far more sophisticated tools and programs to carry out attacks that would attempt to guess any possible password you could’ve used. Two of the most common forms of attacks include:
Dictionary Attacks
Dictionary attacks work by systematically entering every word in a “dictionary” as a password. While these attacks may have originally utilized a standard dictionary, they have evolved to utilize their own specialized dictionaries that consists of data gathered from hundreds of millions of passwords recovered from past data breaches. Some software can also produce common variations, such as substituting numbers for similar-looking letters. These attacks will often leverage their vast library of prior exposed passwords to rank their dictionaries based on which passwords and password techniques are most commonly used, and the guesses will follow in that order.
Brute Force Attacks
Brute-force attacks take it a step further by calculating every possible combination of letters, numbers, and special characters that could make up a password and testing it to see if it is the correct password. As the password's length increases, the amount of time and computing power (on average) to find the correct password increases exponentially.
One might ask themselves, “How could a hacker’s tools possibly make all these guesses when I get locked out after just a few failed attempts?” That is an entirely different topic of conversation, though this article provides a great answer to that question. But as you can see, the world of password security is in a constant arms race between hackers and end users. Hackers are leveraging the latest technology to improve their computing ability and conduct these attacks in shorter time spans with more guesses made, while end users receive new password complexity recommendations (and requirements) from their employers as well as the organizations who administer their accounts. Below is one such recommendation from Microsoft’s Windows 10 security policy settings:
Set Minimum password length to at least a value of 8. If the number of characters is set to 0, no password is required. In most environments, an eight-character password is recommended because it's long enough to provide adequate security and still short enough for users to easily remember. A minimum password length greater than 14 isn't supported at this time. This value will help provide adequate defense against a brute force attack. Adding complexity requirements will help reduce the possibility of a dictionary attack.
While it is great that the Microsoft policy above does consider the threats of both dictionary and brute force attacks, the argument can be made that an end user would be wise to go beyond this minimum 8-character length recommendation. Unfortunately, many online account providers do not require very lengthy passwords. For example, Facebook only requires a 6-character password. The following chart comprised of data from Security.org depicts the time it would take a computer armed with the proper tools to crack a password:
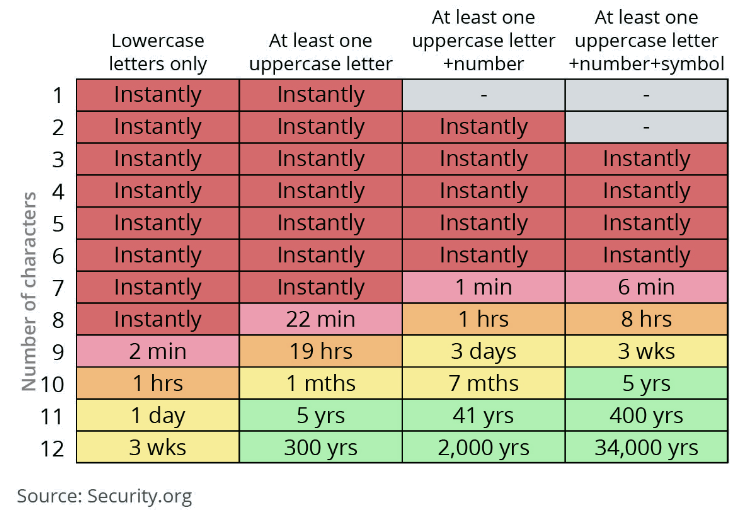
Furthermore, back in 2019 a hacker who goes by the pseudonym Tinker claimed that, "Current password cracking benchmarks show that the minimum eight character password, no matter how complex, can be cracked in less than 2.5 hours" using a hardware rig that utilizes eight Nvidia GTX 2080Ti GPUs. Others have claimed that the computing power needed to crack 8-character passwords can be rented in Amazon's cloud for just $25. Given how fast technological advances have been occurring in the password-cracking industry, the numbers in this chart could be even worse in the near future.
The world will always be full of bad actors with new methods of carrying out attempted cyberattacks. Our account administrators will continue to enhance their minimum requirements for password length and complexity in an effort to meet this evolving threat. However, there is often a gap between what those minimum requirements are, and what the cybersecurity industry would classify as best practices. As end users, we can reduce our risk of an account breach by going above and beyond the minimum complexity and length requirements when creating passwords. As seen in the chart above, the minor inconvenience of a few extra keystrokes upon every login could make the difference between a hacker cracking your password in 1 minute or 34,000 years!
Compass IT Compliance is an industry leader in providing IT security, compliance, and risk management services to organizations of varying size and complexity. Our password policy templates, phishing assessments, security awareness training, and dark web monitoring services provide a holistic approach to swiftly strengthening an organization’s account security. Contact us today to learn more!
Contact Us
Share this
You May Also Like
These Related Stories

9 Easy Steps to Create Strong Passwords
.jpg)
Weighing Your Multi-Factor Authentication Options
.jpg)
.webp?width=2169&height=526&name=Compass%20white%20blue%20transparent%202%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)
.webp?width=610&height=362&name=November%202023%20CTA%20(20).webp)
Comments (1)