How Phishing Emails Can Cost You $40,000
To me, math is what makes the world work. If you think about it, just about everything involves math, especially when it comes to business. When I was going through my MBA program, I really underestimated the amount of math and calculations that you needed to perform for essentially everything. Need to calculate ROI? Math. Need to calculate total cost of goods sold? Math. Need to figure out if Just In Time (JIT) is an appropriate inventory management solution for you? Math. But what about when it comes to the world of Information Security? How much does math matter then, outside of justification for new hardware, software, employees, or services? Turns out, quite a bit actually!
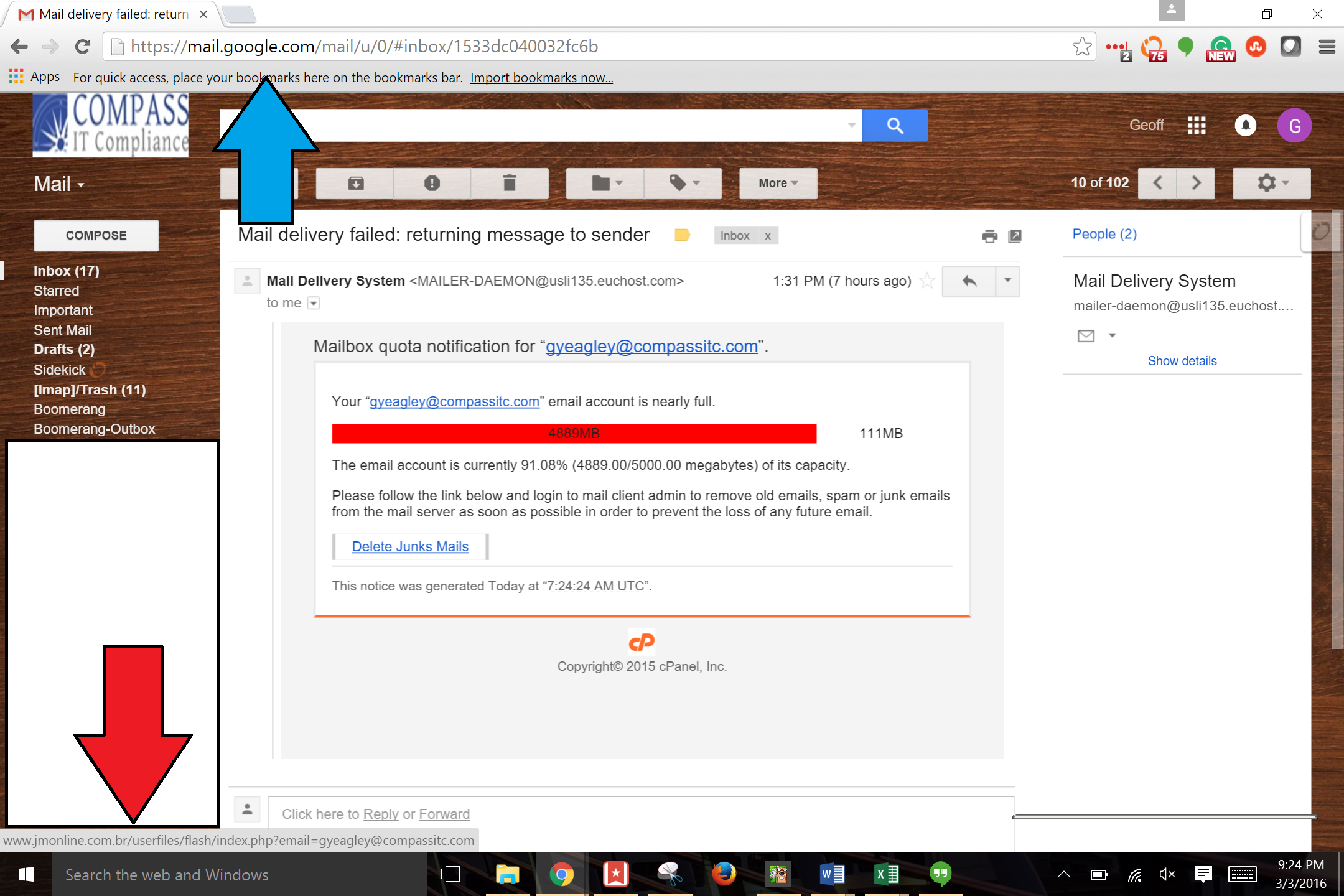
In the past several blog posts, I have discussed the Center for Internet Security Critical Security Controls (CSC's) at length, including what they are, what they mean for your organization, and why they are so important. Today I want to focus on just 1 and share a story that I was told last week that involved a phishing email, a ransomware scheme, and how it cost them upwards of $40,000.
CSC 7: Email and Web Browser Protections. This is the Critical Security Control that I want to discuss and share the experience that I heard about. This CSC discusses in great detail the need to implement web and email filtering, as well as many other defenses, to attempt to identify malicious code and files before a user can surf to a malicious website, click on a malicious link in an email, or open an infected file. Why? So they don't become the victim of malware, specifically ransomware, which is making a huge surge in the information security world these days. So what is ransomware? Ransomware is a type of malware that once activated, restricts a users access to their computer and/or network through encryption and demands the payment of a "ransom" to unencrypt the data. That is pretty straightforward and there have been some very popular cases in the media lately around ransomware, like this one that impacted a hospital in Hollywood and resulted in a $17,000 ransom payment. Now I know what you're probably thinking: In the title, you said $40,000 but now you just said $17,000. How can that be possible? First, I'm glad that you're paying attention. Second, let me explain.
Ransomware: To Pay or Not To Pay?
One of the biggest controversies out there is whether to pay the ransom or not pay the ransom to get your files back. In the paragraph above, the $17,000 is only what was paid in the ransom, not the total cost of trying to get access to the files back through backups, data recovery techniques, etc. In the example that I am going to share, this company used a two prong attack to attempt to recover their data:
- Don't Pay the Ransom - They decided not to pay the ransom and attempt to restore their data through backups that they had. This proved to be a significant challenge as they had to completely reconfigure the server, which did not work. Then they had to install a new server, which cost time and money. Then, once they thought they were good to go and had everything taken care of, they were re-infected the very next day by the same strain of ransomware, this time infecting 5 servers on the network.
- Pay the Ransom - Ultimately, after engaging a local forensics firm at the onset of the ransomware attack and going through what they thought were the appropriate steps, they ended up paying the ransom of $500. Within several hours, they were back up and running (overall) and had access to their data. One person with the organization said that out of the entire process, paying the $500 ransom was the cheapest part of the entire process.
All told, between hiring an outside firm to assist in the process, updating their corporate antivirus, replacing a server, and other tasks, this ransomware infection cost the company around $40,000. Again, paying the ransom, through a BitCoin, was the cheapest part of the entire process. So if this happened to you, do you pay the ransom or not? Well, this post isn't to help you decide as that is a business decision that you have to make should you fall into this position. But, this is just another example of what ransomware can do and how it can significantly impact your business operations and ultimately cost you a ton of money. The FBI suggests that you shouldn't pay the ransom as they don't want to encourage criminal behavior. However, when ransomware hits your organization, you are the one that has to deal with downtime and costs associated with the incident, not the FBI, so it is your decision on how to proceed.
For more information, be sure to check out the infographic below on some tips to prevent ransomware from entering your systems and ultimately your network. Contact us to learn more about the changes to the Center for Internet Security Critical Security Controls!

Contact Us
Share this
You May Also Like
These Related Stories
Phishing Examples: Even the Security Folks Get Targeted

Phishing - Even the Security Folks get Targeted Part II

.webp?width=2169&height=526&name=Compass%20white%20blue%20transparent%202%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)
No Comments Yet
Let us know what you think