Phishing Emails, Ransomware, and the Government
Every day that you turn on the news, there is another story or article about a Ransomware attack that has taken place. Most recently, these stories are focused around healthcare organizations where significant ransoms have been demanded. What we haven't heard much about, but is just as significant, is the threat that Ransomware poses to Government Agencies. From local municipalities to state agencies to federal government agencies, none of these are immune from Ransomware attacks. Before we dig into the details, lets give an overview of what Ransomware is, what the goals are, and how to handle these instances.
What is Ransomware?
Ransomware is a specific form of Malware that installs code on your computer and encrypts any files that are on that specific machine. When that machine connects to a network, the Ransomware can spread throughout the network to other machines. These other machines can be servers that contain billing/payment/client information that can make it hard for you to do business. Ransomware can also spread to your backup, especially if it is stored locally and not offsite which would make your recovery efforts more difficult. Once these files become encrypted, the organization that created or distributed the Ransomware demands a payment, usually in BitCoins, to unencrypt your data. These payments can range from several hundred dollars all the way up to millions of dollars, depending on the size of the organization.
What Ransomware Isn't
When hackers install Malware on machines and systems, the goal is usually to steal some form of sensitive information from the company they are targeting. That is not the goal of Ransomware. The goal of Ransomware is to "lock up" your information, demand you pay for the key to get access to your data (the ransom), and then move on to the next company. Ransomware is a numbers game, pure and simple, designed to make quick money through the ransom payments.
Government Agencies and Ransomware
Ransomware is a numbers game. I know that I already said that but it is true. The faster they can send these emails and create these malicious links, the more cash they can make. In the second 1/2 of 2014, 29 different Federal Agencies saw 321 Ransomware targets. Unfortunately the Federal Government will not discuss if those attacks were successful or not, but, 321 targets is a large number. This has to beg the question: Why are Government Agencies a great target for Ransomware through Phishing Emails? There are a variety of reasons that this takes place, some of which include:
- Low IT Security Budget - Especially at the City and Town level, spending on IT Security and proper Security Awareness training is low
- Low Hanging Fruit - Remember when I said that Ransomware is a numbers game (for the third time?) There are a lot of cities/towns and Government Agencies in this country. This gives these organized crime entities plenty of fish in the sea to go after (did you see what I did there?)
- Time and Resources - Many Government Agencies operate with a small IT Department. This means that there are less people to do the same work which leads to things slipping. In fact, a great example of this would be the Federal website www.healthcare.gov. In September of last year, an audit found the site had significant vulnerabilities that could expose the information of millions of individuals.
The Ransomware risk isn't going anywhere. In fact, it is becoming more and more prevalent on what feels like a daily basis.
What Do We Do Next?
This is the next obvious question. Ransomware and Phishing Emails are our there, what can we as an organization do to protect ourselves, especially if we are a Government Agency. Here are some steps to take:
- Assess Your Risk - Where do you stand with your Information Security Program? How mature is your program at this moment based on the changing threats?
- Assess Your Staff - How do your staff respond to threats that could impact the business? Do you test your staff in a controlled environment to develop a baseline? Have a Social Engineering Assessment completed to assess and remediate your risks
- Be consistent and Thorough - Risk Assessments are great, but they only give you a moment snapshot of how you are doing. Build a culture of security by focusing on security in your staff meetings, newsletters, and other forms of communication. Just like the old saying in Field of Dreams: If you build it, they will come. In this case it might be: If you build it, they will follow it and mitigate your risk!
Ransomware is out there and is more prevalent than ever before. With Government Agencies being a prime target for these hackers, we will see more stories come out about these types of attacks in the coming months. Check out the infographic below for some tips to protect your self from Ransomware. Download it. Print it. Hand it out. Train your staff.

Contact Us
Share this
You May Also Like
These Related Stories
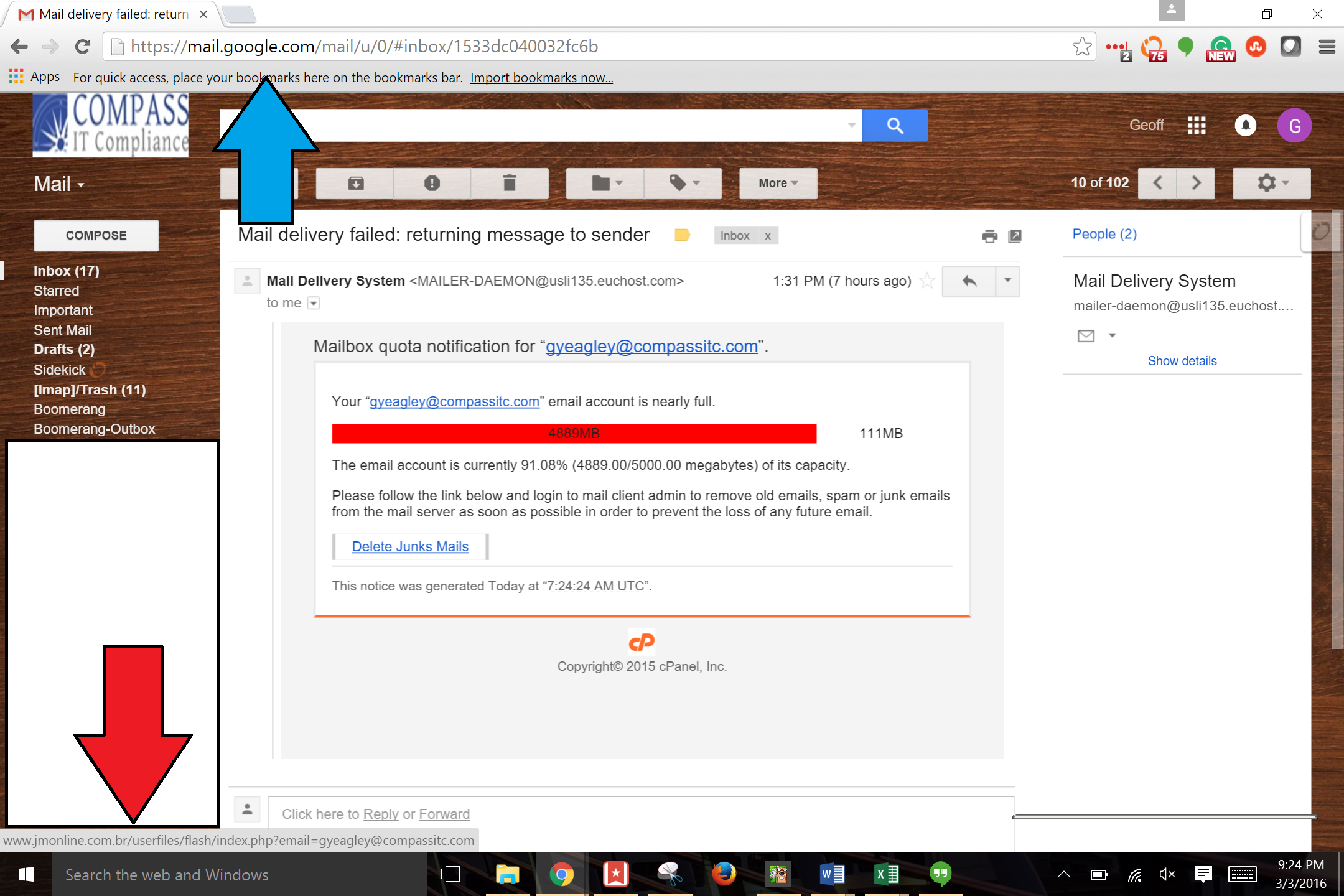
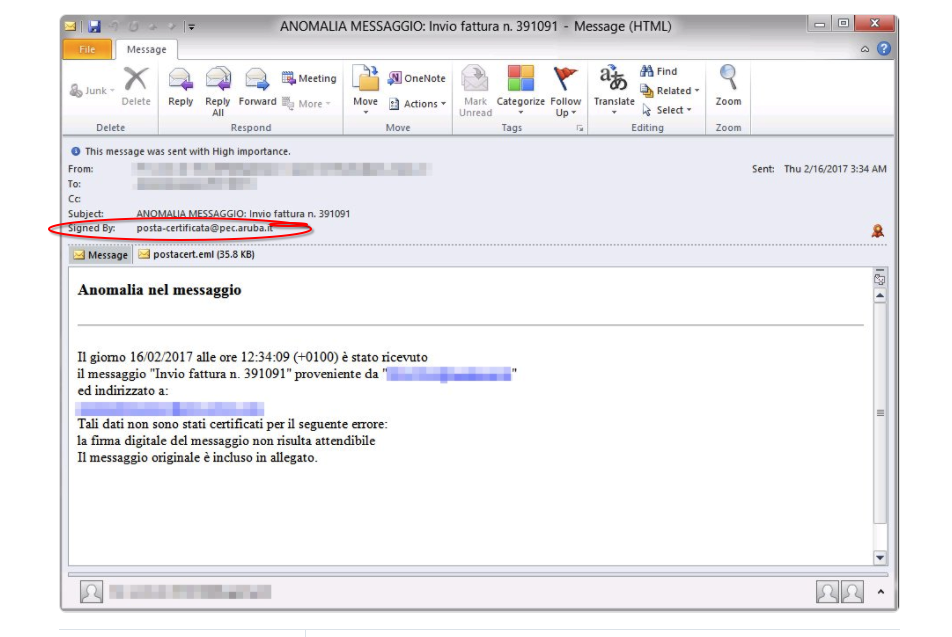
Phishing Examples: Even the Security Folks Get Targeted

How To Prevent Phishing? More Like How To Train Your (Dragon) End-User
.webp?width=2169&height=526&name=Compass%20white%20blue%20transparent%202%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)
No Comments Yet
Let us know what you think