Share this
Next story
What is Social Engineering? Part I →
Fact: Phishing is the number one strategy that bad actors use to deliver malware to your organization.
Fact: Phishing attacks come in a few different forms, known as phishing attacks and spear-phishing attacks.
Fact: Ransomware is the most prevalent and dangerous form of Malware out there today and is the biggest threat to organizations and users.
We all know the facts listed above but honestly, we can never hear them too often. The problem is complacency and thinking, "that can't happen to us." Our guard is down and we receive an email that looks a bit odd (but not too odd) so we click on the link and BOOM….it has happened to us. We have infected our system and potentially our organization's network and files.
Do a search and you will find thousands of blog posts dedicated to Ransomware and Phishing Examples. However, education is key so educating your users to mitigate the risk of an infection is essential. This game is constantly changing and the risks are continuing to evolve. Here are some recent phishing examples so you can personally observe what is happening in real time.
Now that I have thrown some facts at you and hit you with the truth, let's dig into a couple of statistics:
More variations of Ransomware + more people clicking on the link = a major information security problem!
For today's phishing example, we are going to give a shout out to Microsoft for sharing this email with us. While the email is in Italian, the point remains the same: the phishing email was digitally signed, thus making it more difficult to spot as phishy (pun intended!)
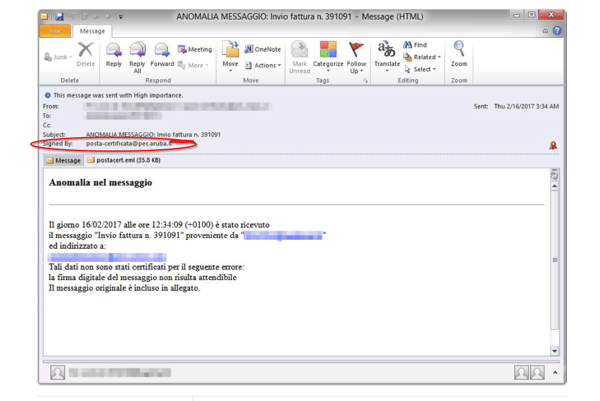
The most critical way to mitigate your risk is to educate your users of the current threats. After educating them, test your users to see if they follow directions to not click on the link. Recently we went through this scenario with a client who guaranteed us that no one would click on the link. Guess what? 50% of the people we sent it to clicked on the link, some more than once. The good news is that it was only us. The bad news is that if it wasn't us, that could have been a disaster for the organization.
These Related Stories


.jpg)
No Comments Yet
Let us know what you think