SolarWinds SUNBURST Hack – And You Thought 2020 Couldn’t Get Any Worse
Co-authored by Derek Morris, Senior Information Technology Security Professional
SUNBURST – add this to the list of all the wonders this year has brought. Are you one of the 18,000 customers infected by SUNBURST? Have you been ordered by the US Department of Homeland Security to quarantine all those systems affected until they have been rebuilt? As you have likely already heard, “On Dec 14, SolarWinds reported that it was a victim of a Cyber-attack which was used to insert malicious code into its legitimate software updates for the Orion software. That malicious code acts as a backdoor that basically allows an attacker to have remote access to the victim's environment. This Cyber-attack was a part of a supply-chain attack, which compromises any organization who uses the Orion software” (Cynet CyOps Team). So, from March through June 2020, while the world was amidst a pandemic and preoccupied with the hysteria, threat actors were inserting malicious code into valid code and distributing it via a trojanized version of the Orion network monitoring application. The malware can lie dormant for up to two weeks after infection and hide in plain sight by masking its reconnaissance attacks as Orion activity.
Companies affected by this vulnerability should have already addressed the issue internally as well as with customers. Otherwise, you would be advised to apply the appropriate patches and perform the recommended system updates as supplied by the vendor immediately. Since pre-existing antivirus software may not detect the threat, it is essential to investigate systems further to identify any residual evidence of the vulnerability. This would include any remaining DLL files left on the system after the update is performed. The following indicators of compromise should be investigated:
- C:\Windows\SysWOW64\netsetupsvc.dll
- name:SolarWinds.Orion.Core.BusinessLayer.dll
- file.properties.certificate.hash: 0fe973752022a606adf2a36e345dc0ed
- file.name:netsetupsvc.dll
- file.path:`C:\windows\syswow64`
- file.properties.certificate.signed: false
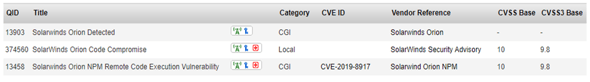
The following QIDs reference the Orion vulnerability and are of urgent severity:
What happens when trust is broken?
A newfound scrutiny of your vendors and the software or services they provide may be on the forefront following the SUNBURST incident. Is this going to move the Zero Trust model to the forefront in more organizations. The statement “immediately shutdown your Orion system or systems” is bold and shows you how big this incident is.
What should you do now?
Start by invoking your incident response plan and getting ahead of this as best you can. Bring the management and leadership groups into the conversation and discuss what message will be sent to your customers. From a tactical standpoint, information security professionals should search through your various security tools and logs for any activity from the Orion system over the past year and look for any indications of this malware. Bringing in a third party security firm such as Compass IT Compliance is always a good idea, as you can utilize the collective experience and education their team possesses to have an unbiased outside set of eyes look things over. Leverage your layers of security controls and tools that you may have in place to see if there is any indication of the SUNBURST malware moving through your network and system. FireEye stated that the SUNBURST malware “masquerades its network traffic as the Orion Improvement Program (OIP) protocol and stores reconnaissance results within legitimate plugin configuration files, allowing it to blend in with legitimate SolarWinds activity”.
A simple and effective way to stay on top of known vulnerabilities and prevent them from affecting your systems is to continue a robust vulnerability management solution. Once measures are taken to remediate the vulnerability, further steps should remain in place to mitigate future risk.
The result of this attack may be an increase in accountability for software vendors. Service level agreements and other contract clauses such as “the right to audit” may start to become more prevalent. Security controls like code review or enhanced testing of application updates may also become pressure points you may want to have vendors in your supply chain attest to. The vendors you are using should have some adherence to compliance standards, whether it be PCI DSS, HIPAA, NIST, or SOC 2 reports. Your organization’s vendor management program should also be revisited to ensure that your vendors are put under the proper examination to help minimize your organization’s risk.
Compass IT Compliance has spent the past decade assisting organization’s small and large in mitigating and overcoming attacks such as this. Our team is currently on standby, ready to answer any questions regarding the recent SUNBURST / SolarWinds / Orion / FireEye attack!
Contact Us
Share this
You May Also Like
These Related Stories
.jpg)
Are You Protecting Your Attack Surface?
.jpg)
When Vendors Get Hacked: Your Guide to Third-Party Data Breaches

.webp?width=2169&height=526&name=Compass%20white%20blue%20transparent%202%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)
No Comments Yet
Let us know what you think