VA Data Breach Exposes the Personal Info of 46,000 Veterans
Being hacked is unfortunately still an all too common occurrence. Even as security measures get stronger, reports of breaches and compromises of individual’s personal information do not seem to be slowing down. As I read about the most recent breach of the Department of Veterans Affairs - in which 46,000 veterans had their personal information (including social security numbers) compromised in an attack announced earlier this month - I can’t help but look back to 2015, when as an active duty service member I was notified that my information had been compromised as part of the Office of Personnel Management (OPM) hack.
The 2015 OPM attack was not just a minor breach; the attackers gained access to millions of service members SF-86 forms which hold as much personally identifiable information (PII) as an attacker could ever dream of. This form goes so deep that I had to list details about an ex-step-sister that I had not seen or spoken to in 20 years.
Fast forward to 2020 and now I am sadly expecting a letter from the VA letting me know that my personal information has been compromised once again. Given what has taken place, I will now have to pay close attention to all my accounts to watch for any fraudulent activity that may result from my data being exposed. I should be mad and/or annoyed, but I am honestly not. Maybe it is because I work in the cybersecurity industry and see it all the time, but I understand that these things happen. The question I do have though, is why does this continue to occur? Is it negligence?
According to what we have been told so far, the VA breach originated from the department’s Financial Services Center (FSC). The FSC determined one of its online applications was accessed by unauthorized users to divert payments to community health care providers for the medical treatment of veterans. It is believed that the attackers gained access to the application to change financial information by using social engineering techniques and exploiting authentication protocols. Social engineering is most commonly carried out via phishing (emails) and vishing (phone calls). The FSC is notifying the affected individuals, including the next-of-kin of those who are deceased, of the potential risk to their personal information. Veterans whose information was involved are advised to follow the instructions in the notification letter to protect their data.
Unfortunately, we live in a world where the offense is always going to be ahead of the defense, at least when it comes to cybersecurity and dealing with hackers. Hackers have always been skilled, but in this day and age many have grown the hobby into a full-time profession. Not only are they professionals, but they are professionals trying to make a name for themselves. The bigger the name, the bigger the target, and the bigger the recognition is (and often the financial reward too). The Department of Veterans Affairs is a fine example of this.
For another example of a cyber-attack on a big-name target, look back to earlier this year when the Saudi hacker group “OurMine” compromised the twitter accounts of nearly half of the teams in the National Football League. Though the exact cause of the attack has not been confirmed, Twitter confirmed that the accounts were hacked by a third-party platform.
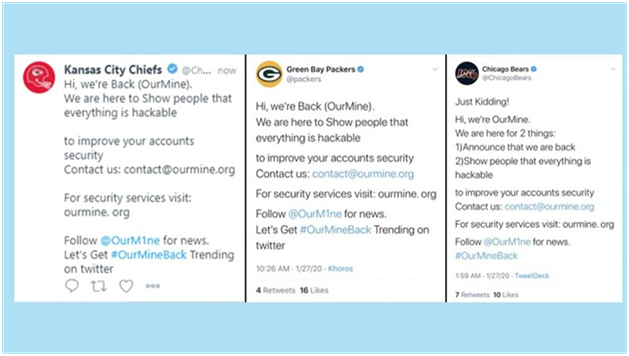
OurMine was simply advertising for their commercial services. Brilliant or stupid? All I know is I saw it on NBC News on a Sunday morning in January and had never heard of OurMine before that. It explains the whole reason you go after these recognizable targets. I will now remember the name of this group and associate them with this very recognizable hack.
Just because you are not as recognizable as the federal government or the NFL does not mean you are safe from being a target. If there is a way a group or an individual can benefit financially from compromising your accounts and data, then you are a target. The best thing you can do is stay vigilant and implement security measures to help protect your business, your employees, and your customers. Do not be negligent! Do not ignore the security best practices that exist to guard against the bad guys. Here are some tasks organizations should be doing to help mitigate the risk of a breach:
- Cybersecurity Awareness Training – Educate your employees regularly and give them the training to notice things like phishing emails, social engineering scams, and other types of attacks
- Two-Factor Authentication – Adding the extra layer of security goes a long way in preventing unauthorized access
- Vulnerability Scanning and Penetration Testing – Identify vulnerabilities through scanning and test the security of your system with an annual penetration test (at minimum)
- Security Patching – Known security vulnerabilities give the hackers an easy entry into your system and all the information it contains; patches will fix those identified security vulnerabilities
Compass IT Compliance has spent the past decade helping organizations across the nation to mitigate their IT security risks and strengthen their organizational security posture. Contact us today to learn more and discuss your unique situation!
Contact Us
Share this
You May Also Like
These Related Stories
.jpg)
It (Should) Be an MFA World, We Are Just Living in It

Cyber & Physical Security: Why You Need Both

.webp?width=2169&height=526&name=Compass%20white%20blue%20transparent%202%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)
.webp?width=610&height=362&name=November%202023%20CTA%20(3).webp)
No Comments Yet
Let us know what you think