Phishing vs. Pharming: What's the Difference?
Online security is a prime concern for individuals and organizations alike with cyber threats and scams targeting users often. Two prevalent cyber threats, phishing, and pharming, pose significant risks to users by attempting to deceive them into revealing sensitive information. Although they share the ultimate objective of data theft, phishing, and pharming employ different methods to achieve their goals. In this blog post, we will explore the differences between phishing and pharming, and offer practical insights into safeguarding against these pervasive online dangers.
What is Phishing?
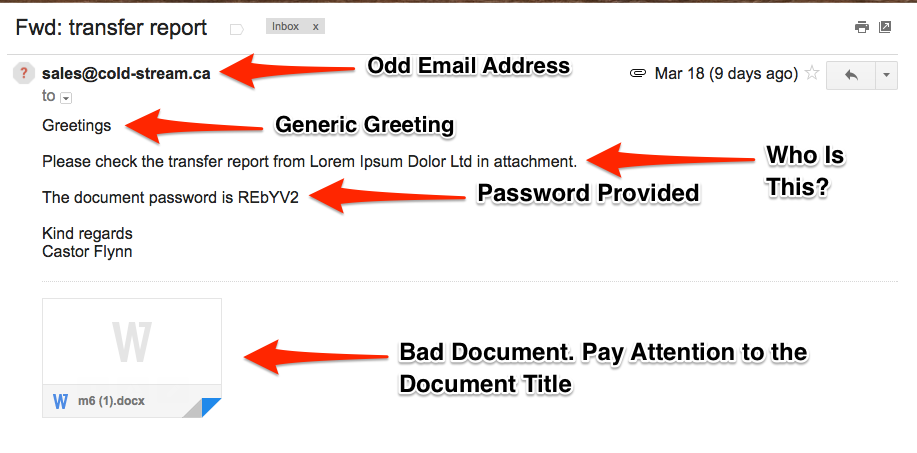
Phishing is a type of cyberattack where an attacker attempts to deceive individuals into providing sensitive information, such as usernames, passwords, credit card numbers, or other personal details, by pretending to be a trustworthy entity in electronic communications. These attacks often occur via email, social media, or other online platforms, where the attacker poses as a legitimate organization, friend, or service. The goal is to trick the recipient into clicking on malicious links, downloading infected attachments, or revealing confidential information. Beyond mimicking company logos and layouts, phishing attempts often employ persuasive language and urgent calls to action, compelling recipients to divulge sensitive information such as login credentials, financial details, or personal data.
Phishing scams are designed to trick you into giving up sensitive information by pretending to be a trustworthy entity. Here are five of the most common phishing tactics you might encounter:
- Financial Institution Scams: These phishing emails appear to come from banks or financial institutions, urgently requesting you to update your account information or verify transactions. They often create a sense of urgency to prompt quick action without thinking.
- Shipping Notifications: Impersonating delivery services like FedEx or UPS, these messages inform you of a package delivery or shipment status update. They typically contain a link to track the package, which, when clicked, can install malware or steal your information.
- Tech Support Scams: These messages pretend to be tech support alerts from well-known companies such as Microsoft or Apple. They warn of security threats on your device and urge you to click a link or call a specified number for assistance, leading to potential data theft or malware installation.
- Lottery or Prize Scams: These phishing emails claim you have won a lottery or prize, asking for personal information or a fee to claim your winnings. They exploit the excitement of an unexpected win to extract sensitive information.
- Social Media Account Verification Scams: These emails appear to be from popular social media platforms like Facebook or Instagram, asking you to verify your account or reset your password due to alleged security concerns. This can lead to account takeover if you provide your login credentials.
Examples of Phishing Attacks
The Nordea Bank phishing incident in 2007 was a significant cyberattack in which hackers stole approximately $1.1 million from customers of Nordea Bank, the largest financial services group in the Nordic region. Attackers sent phishing emails disguised as official communications from the bank, prompting recipients to download a malware-infected security software update. This malware, a Trojan horse, captured customers' login credentials, allowing the hackers to access and drain their accounts.
The 2011 RSA phishing incident was a major cyberattack in which hackers targeted RSA, a leading security company known for its SecurID authentication tokens. Attackers sent spear-phishing emails to RSA employees, containing a malicious Excel attachment titled "2011 Recruitment Plan." When opened, the attachment exploited a zero-day vulnerability in Adobe Flash, installing a backdoor that allowed the attackers to gain access to RSA's network. The breach resulted in the theft of sensitive data related to RSA's SecurID tokens, compromising the security of millions of users and forcing RSA to replace the tokens for many of its customers.
The 2014 Sony phishing incident was a high-profile cyberattack where hackers infiltrated Sony Pictures Entertainment's network, resulting in a massive data breach. The attackers sent spear-phishing emails to Sony employees, tricking them into clicking on malicious links that installed malware on the company's systems. The breach led to the theft of a vast amount of sensitive information, including unreleased films, employee data, internal emails, and executive salaries. The hackers, who identified themselves as the "Guardians of Peace," leaked the stolen data publicly, causing significant embarrassment and financial damage to Sony.
How to Protect Against Phishing
Educating yourself about these common phishing tactics is crucial for staying safe online. Here are some steps to protect yourself:
- Be Cautious with Emails and Messages: Avoid opening emails or messages from unknown senders. Do not click on links or download attachments from suspicious sources.
- Verify Requests for Personal Information: Never provide personal information in response to an unsolicited request. Contact the company directly using official contact information to verify any request.
- Report Phishing Attempts: If you believe you have been targeted by a phishing scam, report it immediately. This helps prevent others from falling victim to the same scam.
- Monitor Your Accounts: Regularly check your bank and other financial accounts for unusual activity. Many institutions offer alerts for suspicious transactions, which can help you catch potential fraud early.
By staying vigilant and informed, you can protect yourself and others from falling victim to phishing scams.
What is Pharming?
Pharming is a cyberattack technique used to redirect a website's traffic to a fake website without the user's knowledge. Unlike phishing, which relies on tricking individuals into clicking on malicious links, pharming manipulates the resolution of domain names to direct users to fraudulent sites, even if they enter the correct web address.
Here's how pharming works:
- DNS Poisoning: Attackers corrupt the Domain Name System (DNS) by altering the IP address associated with a domain name. When users try to visit a legitimate website, they are redirected to a fake site that looks identical to the real one.
- Malware Infection: Attackers can also use malware to modify a user's local host file, which maps domain names to IP addresses. This way, even if the DNS itself is not compromised, the user's device will still redirect them to a malicious site.
Pharming can be particularly dangerous because it is more difficult for users to detect compared to phishing. The fake websites used in pharming attacks are often designed to look exactly like legitimate ones, making it hard for users to realize they have been redirected.
Examples of Pharming Attacks
In February 2007, a sophisticated pharming attack targeted around 65 financial institutions across the United States, Europe, and Australia. Hackers launched the attack using multiple IP addresses and server sites in four countries to distribute fraudulent spam emails. These emails contained false news stories, such as the Australian Prime Minister's health crisis and an Australian cricket match, luring recipients to click on links that redirected them to malicious websites. Once users' machines were infected with malware, any information entered into legitimate banking sites was also sent to the hackers. The attack compromised over 1,000 machines within a single day before authorities managed to shut it down on February 21. Major targets included Barclays Bank, the Bank of Scotland, PayPal, eBay, Discover Card, and American Express, with most victims located in Australia and the United States.
In 2008, a drive-by pharming attack in Mexico targeted users by exploiting a vulnerability in 2wire modems. This attack spread through spammed emails disguised as electronic postcards from Gusanito.com, a popular eCard website. When users clicked the link to view the supposed postcard, they were directed to a spoofed Gusanito page that loaded malicious Flash files. These files modified the 2wire modem localhost table, redirecting users to fraudulent sites whenever they attempted to access pages related to Banamex.com, the same banking site targeted in a similar attack two months earlier. The malicious Flash file was detected as SWF_ADHIJACK.D, and all related malicious URLs were blocked.
In 2015, a sophisticated pharming attack targeted home routers distributed by Brazil's largest telecommunications company, Oi. The attack aimed to redirect web traffic by altering DNS settings through malicious modifications. This campaign, observed over a five-week period starting in December, began with phishing emails warning recipients of past-due accounts, prompting them to visit a portal. These emails led to websites that executed cross-site request forgery attacks, exploiting vulnerabilities in UTStarcom and TP-Link routers. The attackers used iframes with JavaScript to exploit these vulnerabilities and attempted to brute force the router's admin page using default credentials. Once access was gained, they changed the primary DNS setting to an attacker-controlled site and the secondary to Google's public DNS. This method ensured DNS requests would resolve even if the malicious server failed, minimizing detection. The attack, primarily aimed at harvesting banking credentials, was nearly invisible to users, with the only defense being changing the default router password.
How to Protect Against Pharming
- Use Secure DNS Services: Opt for DNS services that offer protection against DNS poisoning and provide more secure and accurate DNS resolution.
- Keep Software Updated: Ensure that your operating system, browsers, and security software are regularly updated to protect against vulnerabilities that could be exploited in pharming attacks.
- Use HTTPS: Look for HTTPS and the padlock icon in the browser address bar, which indicate a secure connection. However, be aware that even HTTPS can be spoofed by sophisticated attackers.
- Educate Users: Awareness and education about pharming and other types of cyberattacks can help users recognize potential threats and take appropriate precautions.
By understanding pharming and taking proactive measures, individuals and organizations can better protect themselves from this type of cyber threat.
What’s the Difference Between Phishing and Pharming?
In the realm of cybersecurity, both phishing and pharming are malicious tactics used to steal sensitive information, but they employ different methods and have distinct characteristics. Key differences between phishing vs. pharming include the method of attack and user involvement. Phishing relies on deceptive emails or messages to trick users into taking action, whereas pharming manipulates DNS or local host files to redirect users automatically. In phishing, detection is possible by vigilant users who recognize suspicious emails or links, while pharming is harder to detect because it occurs at a technical level, often without any obvious signs to the user. To protect against phishing, it is essential to be cautious with unsolicited emails and messages, avoid clicking on suspicious links, and verify requests for personal information. To guard against pharming, using secure DNS services, keeping software updated, looking for HTTPS in the address bar, and being aware of unusual website behavior are crucial steps. Understanding these differences is key to staying safe online.
%20(1).webp?width=610&height=660&name=Phishing%20vs%20Pharming%20comparison-02%20(1)%20(1).webp)
How Is Pharming Similar to Phishing?
Both pharming and phishing tactics aim to exploit unsuspecting individuals and extract sensitive information, such as login credentials or financial data, for nefarious purposes. Whether through deceptive emails in the case of phishing or manipulation of internet infrastructure in pharming, cybercriminals seek to deceive users into unwittingly divulging valuable personal information.
Additionally, both phishing and pharming pose significant risks to individuals and organizations and can result in monetary loss, identity theft, or unauthorized access to sensitive accounts. While the techniques used may differ, the underlying threat posed by phishing and pharming underscores the crucial importance of having robust cybersecurity controls and informed users.
In Conclusion
Understanding the differences between phishing and pharming is crucial for protection against cyber threats. While these tactics may differ in execution, their shared goal of exploiting unsuspecting individuals highlights the need for strong cybersecurity measures. It is best to remain vigilant and implement robust security protocols to mitigate risks. At Compass IT Compliance, our team of professionals is dedicated to assisting organizations in strengthening controls, educating users, and fostering a strong security culture. Contact us today to learn more about how we can support your cybersecurity needs.
Contact Us
Share this
You May Also Like
These Related Stories
.jpg)
Receiving a Scam Text… From My Own Phone Number

What Is a Whaling Attack? (With Examples)
.webp?width=2169&height=526&name=Compass%20white%20blue%20transparent%202%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)

No Comments Yet
Let us know what you think