CMMC: Moving Away from Self-Assessments
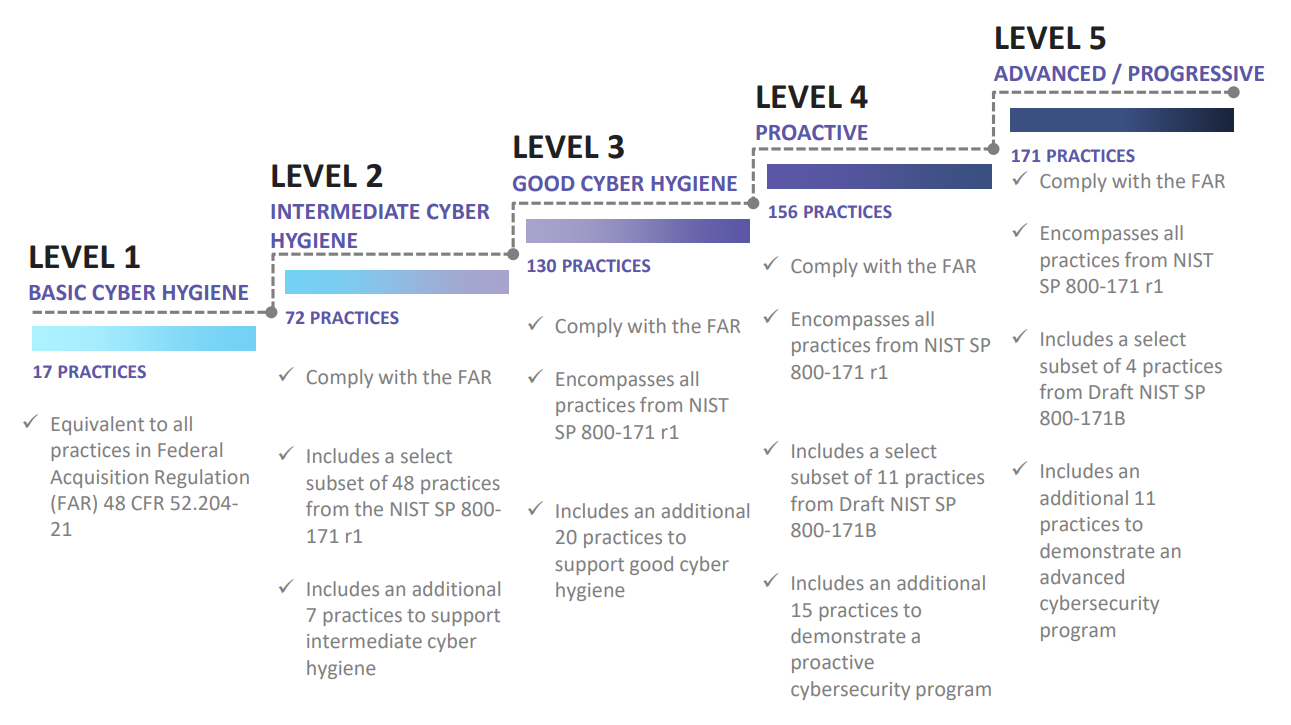
The Cybersecurity Maturity Model Certification (CMMC) is a certification procedure developed by the Department of Defense (DoD) to certify that contractors working with the DoD have the controls in place to protect sensitive data, also referred to as controlled unclassified information (CUI). The CMMC Model is based on the best-practices of different cybersecurity standards, including NIST SP 800-171, NIST SP 800-53, ISO 27001, ISO 27032, AIA NAS9933, and others into one cohesive standard for cybersecurity. The CMMC Model has five defined levels, each with a set of supporting practices and processes. Practices range from Level 1 (Basic Cyber Hygiene) to Level 5 (Advanced/Progressive). To meet a specific CMMC level, an organization must meet the practices and processes within that level and all levels below. The DoD will specify the required CMMC level an organization must possess when releasing Requests for Information (RFIs) and Requests for Proposals (RFPs).
One of the biggest changes to come with the release of CMMC is the replacement of the previous self-attestation model with a shift to certification via CMMC Third Party Assessment Organizations (C3PAOs). Prior to CMMC, the DoD enacted the Defense Federal Acquisition Regulation Supplement (DFARS) clause 252.204-7012 (2016), requiring DoD contractors and subcontractors to implement the security controls identified in NIST SP 800-171. However, NIST SP 800-171 compliance was only required to be validated via self-attestation from the contractors and subcontractors.
In the summer of 2019, the DoD decided to conduct an audit on ten contractors with DoD contracts worth $1 million or more to assess their level of compliance with the controls outlined in NIST SP 800-171. What they found was that 9 of the 10 contractors did not consistently implement DoD‑mandated system security controls for safeguarding Defense information. The DoD audit report identified deficiencies at the nine contractors they assessed related to:
- Using multifactor authentication
- Enforcing the use of strong passwords
- Identifying network and system vulnerabilities
- Mitigating network and system vulnerabilities
- Protecting CUI stored on removable media
- Overseeing network and boundary protection services provided by a third-party company
- Documenting and tracking cybersecurity incidents
- Configuring user accounts to lock automatically after extended periods and unsuccessful logon attempts
- Implementing physical security controls
- Creating and reviewing system activity reports
- Granting system access based on the user’s assigned duties
The audit report went on to note that the DoD Component contracting offices and requiring activities did not establish processes to:
- Verify that contractors’ networks and systems met National Institute of Standards and Technology (NIST) security requirements before contract award
- Notify contractors of the specific CUI category related to the contract requirements
- Determine whether contractors access, maintain, or develop CUI to meet contractual requirements
- Mark documents that contained CUI and notify contractors when CUI was exchanged between DoD agencies and the contractor
- Verify that contractors implemented minimum security controls for protecting CUI
In a nutshell, the audit found that the previous system of NIST SP 800-171 self-attestation/assessment was not working. DoD contractors were not implementing the controls that they claimed to be implementing or were overstating their efforts, and the DoD Component contracting offices were not verifying contractor compliance and communicating requirements as needed. These alarming findings reinforce the DoD’s decision to develop CMMC and require certification assessments to be conducted by CMMC Third Party Assessment Organizations (C3PAOs). This will mitigate the risk of a biased or insufficient assessment and ultimately create an environment where sensitive DoD data is better protected. DoD contracts will now state the necessary CMMC level required, and contractors will be required to provide proof of a passing CMMC third party assessment for that CMMC level before even being considered for the contract.
Does this mean that self-assessments are a thing of the past? No. The self-assessment still holds great value in helping an organization prepare for their official CMMC assessment. The self-assessment can help identify controls that need implementation or improvement prior to the official assessment and will help mitigate the risk of a failed CMMC assessment or a lengthy remediation process that might delay the contractor’s ability to bid on an RFP.
Though the application process has just begun, Compass IT Compliance is currently on track to become a CMMC Third Party Assessment Organization (C3PAO). In the meantime, we are assisting contractors across the nation with our CMMC Readiness Risk Assessment. Our highly experienced auditors assess your current level of compliance with the latest Cybersecurity Maturity Model Certification release, identifying gaps in controls and key work areas that your organization must address to prepare for the upcoming release of the CMMC. Contact us today to learn more!
Contact Us
Share this
You May Also Like
These Related Stories
%20Score.jpg)
Reporting Your DoD Self Assessment (SPRS) Score: What to Know

What is TISAX Assessment Level 2.5 (AL 2.5)?

.webp?width=2169&height=526&name=Compass%20white%20blue%20transparent%202%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)
No Comments Yet
Let us know what you think