CMMC – What Is It, and Why Does It Matter?
There has been a lot of discussion around the cybersecurity interwebs lately about something called CMMC. CMMC stands for Cybersecurity Maturity Model Certification, which sounds super fancy and important, but what does it really mean?
The Cybersecurity Maturity Model Certification (henceforth referred to as CMMC for brevity) was designed by the Department of Defense in an attempt to recognize the importance of cybersecurity controls in all partner, contractor, and subcontractors that deal with the DoD. As many of you are aware, the NIST 800 series of controls have been around for a while and have been guidance for a strong security program. What the DoD had discovered was that because there was no certification for the controls, many companies were performing self-assessments without understanding the controls and how to keep data safe and secure. Going forward, the DoD is going to require a level of CMMC certification in their contracts to ensure compliance.
This is not the first time the government has worked to set up standards. In addition to NIST guidelines, specifically NIST 800-171 and NIST 800-53, back in 2016 the government also put out DFARS, or the Defense Federal Acquisition Regulation Supplement. The primary goal of DFARS was protecting Controlled Unclassified Information, or CUI. It stressed protecting the data flowing through and stored in the contracted business, and how breaches are responded to. It too was largely based on NIST 800-171, and could be completed through a self-assessment process, although they did recommend outside assistance.
Now comes along CMMC. The CMMC builds upon the NIST 800-171 base with some DFARS guidance, some ISO 27000 series controls, and even some FISMA information. There are two big differences between CMMC and all that have come before it:
- CMMC is a framework with a certification – Like ISO 27001, this framework is going to have a certification process. Authorized organizations and assessors are being set up today to be able to perform certification assessments. These certifications, again like ISO, will be good for three years, and will demonstrate to the DoD and others that your organization has gone through the certification process and come out the other side.
- CMMC has maturity levels – The DoD is being as direct as they can be, putting both “Maturity” and “Certification” right in the title to avoid any ambiguity! They do understand that in some cases, organizations may have little to no information that is confidential. They might also have information that could cripple certain agencies if released into the wild. So, there will be 5 levels of certification, with level 3 being the default level. Level 3 certification pretty much follows the NIST 800-171 guidance with some additional controls, which CMMC refers to as practices. To make it easy to understand, each level has a different number of practices required for certification, so rather than take a control and try to modify it between levels, the CMMC uses separate practices. The graph below shows the different levels:
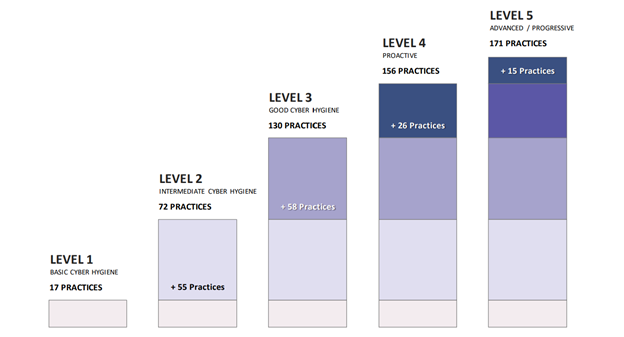
The graph below shows the different domains in the CMMC, and how many controls are in each domain at each level. If you are familiar with ISO 27XXX, DFARS, or NIST 800-171 or 53, you will recognize these domains very easily:
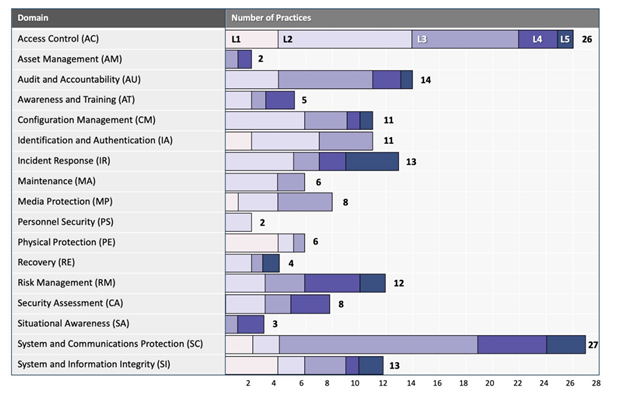
As you can see, there are many areas that if you are dealing with the DoD or affiliates in any way, you should already be looking into. So, what should your next steps be?
- DO NOT allow a company to offer you a certification yet – The applications for certification companies just went up this week (June 23, 2020), and there is still work to do before they are ready to perform certification assessments. Assessment companies will be referred to as Certified Third-Party Assessor Organization, or C3PAO (not only did I get another acronym in, but I also refrained from making a Star Wars joke). Just like your organization, the assessment organizations will also have to be certified. There is a pilot program in the works to get some firms up and running quickly, but if you are contacted about certification, please understand there is no one currently authorized to do so (as of the date this blog is being posted; you may read this months from now and this comment will be irrelevant as assessors will become certified).
- Review your current security posture – If you are NIST 800-171 compliant (really compliant, not just on paper) and DFARS compliant, you are going to have a leg up on those companies that are not. The CMMC is good at showing the extra gaps between the frameworks, so see what else you may be missing in advance.
- You CAN act proactively and have an uncertified CMMC assessment completed – In fact, the CMMC accrediting body is all for it! The domains and practices are published and are currently at version 1.02. Compass IT Compliance can assess your organization to these practices, risk assess any gaps, and make recommendations on how to remediate them prior to the actual certification requirement.
The bottom line is that the CMMC framework is an excellent set of cybersecurity controls. If you have been going through the NIST and DFARS assessments already, there should not be any heavy lifting to get to CMMC maturity level 3. If you have not been working on these in the past, now is the time to review the controls because the biggest change is that instead of taking your word for it via self-assessments, you will now be required to have a third-party assessment attest to your compliance, much like PCI and ISO. Contact us today to learn more about CMMC and discuss your unique situation!
Contact Us
Share this
You May Also Like
These Related Stories

An Introduction to CMMC Compliance
%20Score.jpg)
Reporting Your DoD Self Assessment (SPRS) Score: What to Know

.webp?width=2169&height=526&name=Compass%20white%20blue%20transparent%202%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)
No Comments Yet
Let us know what you think