Share this
Previous story
← Phishing Examples: Google Docs Scam

Friends of Compass,
There is a rash of ransomware attacks being reported that has affected as many as 74 countries. One of the largest reported sectors is hospitals within the United Kingdom, with at least 16 hospitals affected. Many hospitals report being disabled and unable to perform regular functions (phones shut down, pen and paper notes only, and patients asked not to come to the emergency rooms). Other areas affected include a telecom company in Spain, and some FedEx computers as well. This attack does not seem to be targeted to any specific industry or company.
Ransomware is computer malware that installs on a victim's system and runs a program that holds the victim's data hostage and sends a message of extortion to the user until a ransom is paid. Simple ransomware may lock the system in a way which is not difficult for a knowledgeable person to reverse, and display a message requesting payment to unlock it. More advanced malware encrypts the victim's files, making them inaccessible, and demands a ransom payment to decrypt them.
Early investigation leads security staff to believe that this is a variant of ransomware called Wanna Decryptor (also called WannaCry), a relatively recent addition to ransomware. There is a theory that this strain is being spread through a vulnerability in the Microsoft Secure Message Block (SMB) service, which was patched with Microsoft Security Bulletin MS17-010 back in March. A screenshot of the ransomware is below:
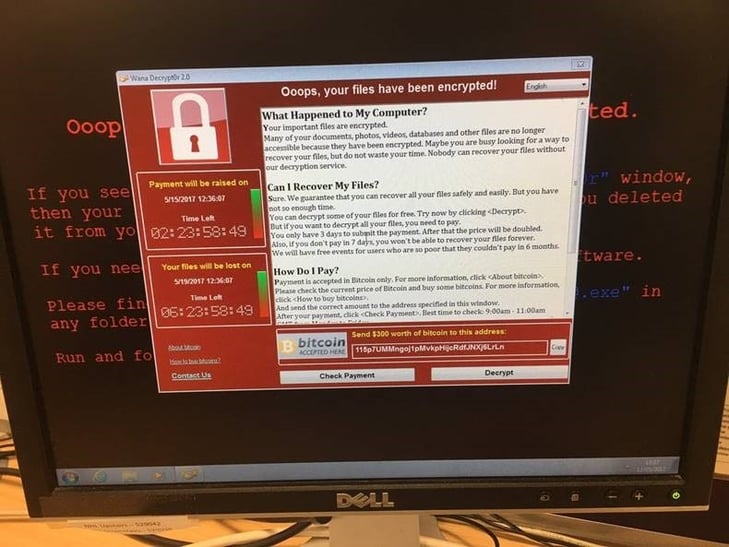
Currently, the malware is easily removable from the systems, but removing the malware does not decrypt the files. As of this writing, the only way to decrypt the files is pay the ransom, or restore files from a clean backup.
Compass recommends taking the following steps to protects systems and files from ransomware:
What to do if compromised:
Compass can provide the following services to assist with the prevention of ransomware:
If you have any questions on this or any other IT Security topics, please don't hesitate to contact us. Also, don't forget about our upcoming webinar that is focused on the latest threats in Social Engineering. Be safe and secure and register below!
Compass IT Compliance
www.compassitc.com
These Related Stories



No Comments Yet
Let us know what you think