While there are many antivirus solutions available on the market, we know that not every solution can detect and remove every type of malware. Therefore incident response tools are important to keep in your arsenal. Simply scanning, detecting, and removing viruses or malware is not enough in today’s threat landscape. Zero-day and unknown threats with constantly evolving code may still bypass advanced traditional antivirus software. Endpoint detection and response (EDR) tools are becoming increasingly popular and imperative as attack vectors become more and more sophisticated. Not only do EDR solutions include antivirus, but they also include many other security tools such as whitelisting, firewall, website / email filtering, data encryption, blacklisting, device hardening by closing unused ports, and monitoring tools to provide the most comprehensive protection against external threats.
EDR tools are designed to help detect and investigate suspicious activities across all your perimeter endpoints and can be installed on servers, laptops, workstations, etc. EDR solutions are different from antivirus solutions, as they offer more capability, greatly reducing operational deficiencies that arise with having to manage many different policies, signatures, deployments, etc. EDR functions by monitoring network and endpoint events (online and offline) and storing the information on a central database for further analysis, investigation, and reporting. Analytical tools run in the background on the host which monitors data and reporting of potential threats. Traditional antivirus tools use signature or perimeter-based solutions to identify threats, whereas EDR software runs on the client-server model and provides a more in-depth look in real-time response at the vulnerabilities of your network. You can track the threat in real-time and cut off the attack in its early stages before it becomes a critical event by removing the device from the network and isolating the system. This feature allows you to review the root cause of the attack and utilize forensic data collected and needed in forensic investigations.
With the increase in remote workforces and more and more endpoints operating outside of a secured network, the digital perimeter has never been more at risk. To gain control of your assets, it is recommended to consider a holistic approach to endpoint security. EDR solutions can serve as a replacement or complement to your current security measures. Since EDR works where antivirus fails, you should expect to receive alerts that the endpoint has been compromised. An example is below:
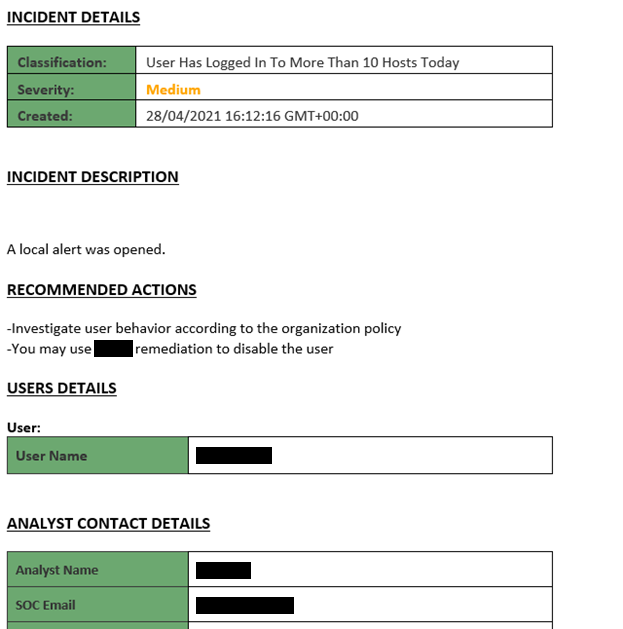
Compass IT Compliance works very closely with our partners in the EDR industry to find the best solutions to meet the complex needs of our clients. Interested in learning more about antivirus, EDR, or any other malware-related topics? Feel free to contact us to discuss your unique situation!
These Related Stories



No Comments Yet
Let us know what you think