Share this
Next story
What is PCI Compliance? →
The seemingly most common way for an attacker to use social engineering to gain entry, exfiltrate information or disrupt business is through email phishing. As I mentioned in the previous blog, slick tactics like using nicknames and shockingly proper grammar are some of the more nefarious ways email phishing is successful.
In the past, phishing emails were easily identifiable. They used massive amounts of emails blasted out to see if a few would get clicks or hits. Attributes like poor grammar, less focused messages and easily identifiable bad email addresses were used. Here is a great example of a BAD phishing email:
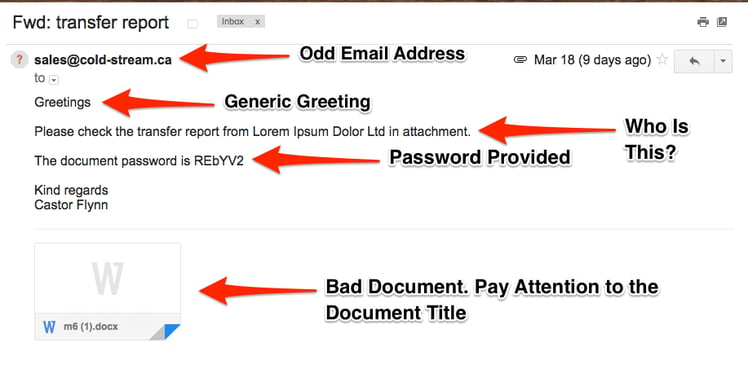
Today, phishing emails are getting more focused toward the intended target and are being called Spear Phishing. The email addresses used to send from almost seem real and the message itself has an overall sense of being legit. Social media or public information about a person is being utilized more often to create a seemingly real message about something that needs to happen. Below is an example that one of the Compass Auditor’s received, allegedly from Amazon:
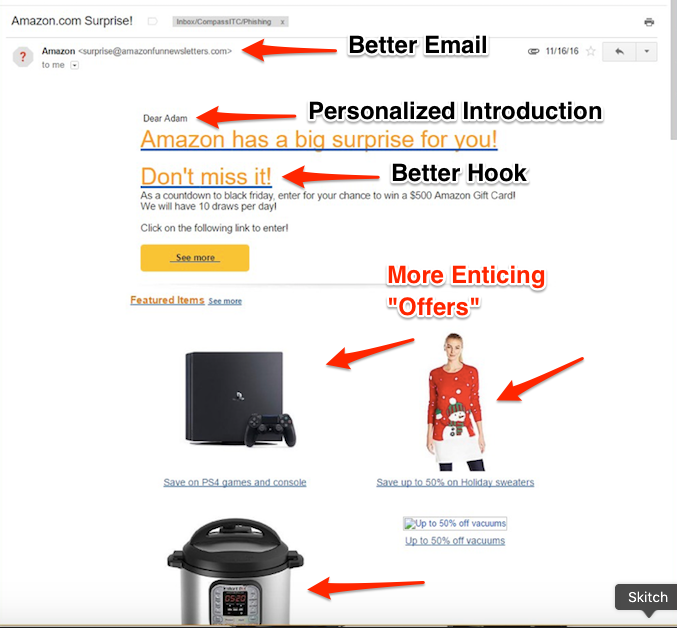
While this is still not the best, as you can see, it is more personalized, appears to be more legitimate, and provides pictures of items that a person might be interested in, further enticing them to click on any link or picture in the email.
I shared an example phishing email in part I of the blog series, but I want to share it again with you as it illustrates how sophisticated these phishing emails are getting. I was working with a client who shared an instance of an executive’s assistant receiving an email while sitting outside of a meeting that the executive was attending with a very specific type of client. The email was from the executive, call him Peter. Peter was in this meeting at 10am with Steve (made up of course) in conference room 22. Now follow me here… the email to Peter’s assistant looked like it was from Peter and stated something to the sorts of,
“I need you to wire $75,000 dollars to SOandSO@hackerdude.com (made up again), I am in the meeting here with Steve and cannot leave the Conference Room 22 for a while. – Thanks, Peter”
Now anyone of us reading this would probably say, well okay he must need this right now and think it’s a completely valid request. Ultimately, the assistant did not follow through with the request until she spoke with “Peter”. She politely interrupted the meeting to confirm and “Peter” turned out to not be the person requesting this.
This example is the level of sophistication being used, finding out information from people to build the focused phishing attempt. Social media is loaded with this information if you are not being careful. The company that the executive and the assistant worked for had a proper security awareness training and review program. So the assistant was aware and took steps the company defined when put into this situation. So guess what…….as I stated in my last blog, Security Awareness education for your users, co-workers and even your family and friends is the best defense going for battling social engineering phishing attempts.
If you have any questions or need assistance with educating your employees on how to prevent phishing and spear phishing attacks, contact us. Stay tuned for part 3 of the “What is Social Engineering?” blog series where we will discuss phone spoofing and pre-text calling!
Have you seen any good phishing emails out there? Drop us a line in the comments below, but don’t send us any phishing emails :-)
These Related Stories


No Comments Yet
Let us know what you think