MSP Breaches Opening the Door to Further Attacks on Clients
Is your Managed Service Provider (MSP) protecting yours and your client’s data? Are you regularly assessing your MSP and the rest of your vendors? It is no secret that hackers have gained access to more and larger companies over the past few years, but a new malicious tactic is coming to light: once a hacker gains access to an MSP, they can wreak havoc on multiple companies at once, with a single entrance point. MSPs typically have elevated access rights to many, if not all their clients. Multiple clients are managed through a central portal or repository in numerous cases. If the MSP is not employing adequate cybersecurity controls on their systems, all their client systems and data are also at risk. We have already witnessed the devastating effects of supply chain attacks carried out in the SolarWinds and Kaseya incidents that resulted in thousands of customers being put at risk.
MSP Breach Example
This advertisement was recently found on the Dark Web. According to Huntress.com (translated into English), the ad reads:
“Looking for a Partner for MSP processing. I have access to the MSP panel of 50+ companies. Over 100 ESXi, 1000+ servers.
All companies are American and approximately in the same time zone. I want to work qualitatively, but I do not have enough people.
In terms of preparation, only little things are left, so my profit share will be high. Please send me a message for more details and suggestions.”
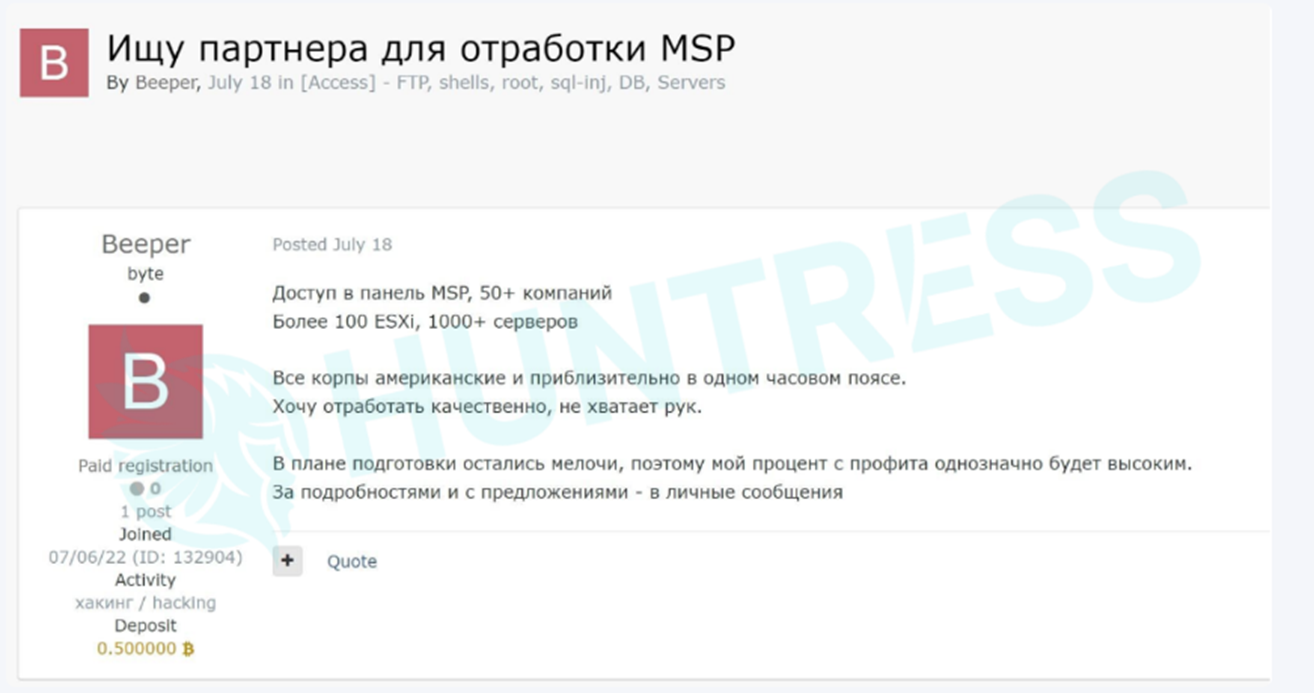
This advertisement and others making the rounds on the Dark Web and Cybercrime forums indicate that attackers are gaining access to MSPs and attempting to broker or sell that access to other malicious customers. While Initial Access Brokers (IABs) have been selling illegitimate access to company systems for quite a while, this new tactic of selling access to multiple companies through a single entrance point is troubling. As MSP and Managed Security Service Provider (MSSP) models become more prevalent and companies begin to rely more on MSPs to secure their infrastructure and data, these types of attacks will also become more prevalent.
Once an attacker has access to an MSP system, it can be inferred that the MSP can be used as a base to jump from client to client. When an MSP client is infiltrated, access can then be obtained to other associated companies that connect with the initial target.
According to CISA Alert AA22-131A, “The cybersecurity authorities of the United Kingdom (NCSC-UK), Australia (ACSC), Canada (CCCS), New Zealand (NCSC-NZ), and the United States (CISA), (NSA), (FBI) are aware of recent reports that observe an increase in malicious cyber activity targeting managed service providers (MSPs) and expect this trend to continue.”
CISA offers several recommendations to MSP customers, such as:
Improving logging and monitoring processes:
- Implement comprehensive security event management that enables appropriate monitoring and logging of provider-managed customer systems;
- Provide visibility—as specified in the contractual arrangement—to customers of logging activities, including the provider's presence, activities, and connections to the customer networks (Note: customers should ensure that MSP accounts are properly monitored and audited); and
- Notify customers of confirmed or suspected security events and incidents occurring on the provider’s infrastructure and administrative networks and send these to a security operations center (SOC) for analysis and triage.
Enforcing MFA:
- Customers should ensure that their contractual arrangements mandate the use of MFA on the services and products they receive. Contracts should also require that MFA be enforced on all MSP accounts used to access customer environments.
Applying the Principle of Least Privilege:
- Customers should ensure that their MSP applies this principle to both provider and customer network environments. Note: customers with contractual arrangements that provide them with the administration of MSP accounts within their environment should ensure that the MSP accounts only have access to the services/resources being managed by the MSP.
Understanding and Proactively Managing Supply Chain Risk:
- Customers should understand the supply chain risk associated with their MSP, including risk associated with third-party vendors or subcontractors. Customers should also set clear network security expectations with their MSPs and understand their MSP’s access to their network and the data it houses. Each customer should ensure their contractual arrangements meet their specific security requirements and that their contract specifies whether the MSP or the customer owns specific responsibilities, such as hardening, detection, and incident response.
While Compass IT Compliance cannot confirm or deny the involvement or relevance to the ad mentioned above, Kansas area MSP NetStandard was hit by a cyberattack on July 26th, 2022. NetStandard described the attack internally to users and clients:
“As of approximately 11:30 AM CDT July 26, NetStandard identified signs of a cybersecurity attack within the MyAppsAnywhere environment. Our team of engineers has been engaged on an active incident bridge ever since working to isolate the threat and minimize impact.
MyAppsAnywhere services, which include Hosted GP, Hosted CRM, Hosted Exchange, and Hosted SharePoint, will be offline until further notice.
No other services from NetStandard have been impacted at this time.
At this point, no additional information on the extent of the impact nor time to resolution can be provided. We are engaged with our cybersecurity insurance vendor to identify the source of the attack and determine when the environment can be safely brought back online.”
Work With Compass IT Compliance to Ensure Your Business is Secure
Serving as an IT security, compliance, and risk management assessor for the past decade, Compass IT Compliance has had the unique opportunity to work with both the clients of MSP and MSSP organizations, as well as many MSPs and MSSPs directly. When evaluating MSPs, it is crucial to verify the steps they take to secure your data and systems while also segmenting your organization from the others they service. We assist organizations across the US in assessing their own risks as well as the risks posed by their MSPs and other critical vendors. Contact us today to discuss your unique cybersecurity challenges!
Contact Us
Share this
You May Also Like
These Related Stories

Another Day, Another Major Ransomware Outbreak...

Ransomware Update: The FBI is Coming, The FBI is Coming...
.jpg)
.webp?width=2169&height=526&name=Compass%20white%20blue%20transparent%202%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)
No Comments Yet
Let us know what you think