Copyright Infringement Scams - All You Need to Know
by Nicholas Foisy on April 24, 2025 at 1:25 PM
In today’s digital-first world, content creators, website owners, and marketers are increasingly becoming targets of sophisticated scams. Among the most insidious are copyright infringement scams—fraudulent schemes designed to deceive recipients into handing over money, credentials, o …
How Accurate Was Netflix's 'Zero Day'? A Realistic Analysis
by Nicholas Foisy on February 25, 2025 at 11:38 AM
Warning: This analysis contains spoilers ahead. Netflix’s Zero Day presents a gripping cyber thriller that blurs the lines between fiction and reality, raising questions about the plausibility of large-scale cyberattacks. This article breaks down the accuracy of the show’s depiction o …
Chinese RedNote App Rises Amid TikTok Ban: New Privacy Concerns
by Peter Fellini on January 17, 2025 at 4:17 PM
As TikTok faces a looming ban in the United States, a new player has emerged on the social media stage: RedNote. Known as Xiaohongshu (Little Red Book) in China, RedNote has skyrocketed in popularity, especially among American users seeking alternatives. However, its meteoric rise com …
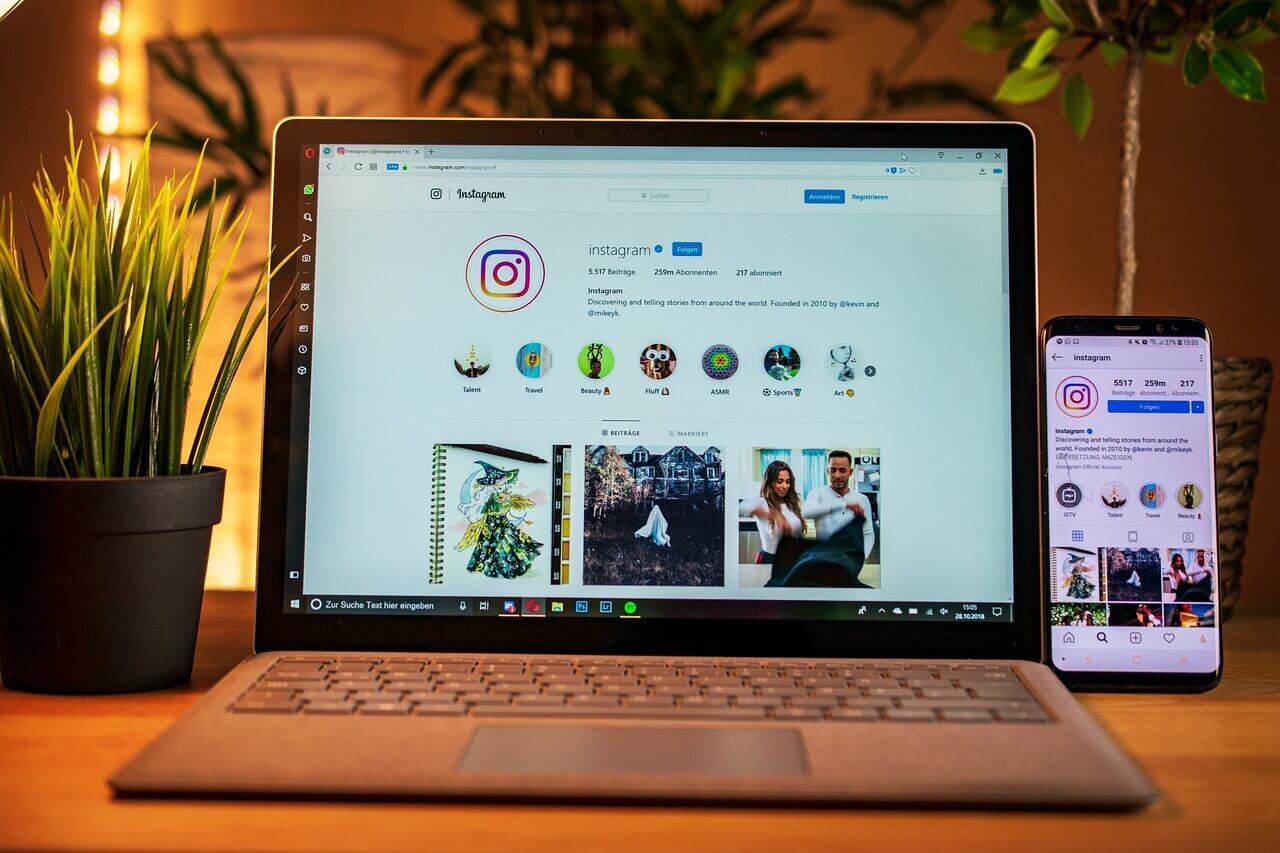
Be Cautious When Following Links on Instagram
by Nicholas Foisy on January 2, 2025 at 2:05 PM
In today's world, Instagram has evolved into more than just a platform for sharing photos and videos. With over a billion active users, it has transformed into a space for networking, marketing, shopping, and even activism. However, with this widespread popularity comes an increasing …
The TikTok Ban: What You Should Know
by Nicholas Foisy on December 16, 2024 at 11:47 AM
TikTok is facing an uncertain future in the United States as a nationwide ban looms. With a January 19 deadline set for its removal from app stores unless parent company ByteDance sells its U.S. operations, the situation has sparked heated debates over privacy, national security, and …
Tesla Optimus Robots - A New Attack Surface for Hackers?
by Nicholas Foisy on October 22, 2024 at 11:10 AM
Tesla's Optimus robot is an ambitious step towards bringing advanced robotics into everyday life, designed to handle repetitive and physically demanding tasks. While it offers exciting potential, it also raises concerns about safety, privacy, and security. As Tesla moves closer toward …
.webp?width=2169&height=526&name=Compass%20regular%20transparent%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)