PCI Compliance Requirements: Some Tools to Help With Requirement 10!
by Derek Morris on March 29, 2017 at 10:00 AM
PCI Requirement 10 states: Track and monitor all access to network resources and cardholder data Logging mechanisms and the ability to track user activities are critical in preventing, detecting and minimizing the impact of a data compromise. The presence of logs in all environments a …
HIPAA Compliance: 5 HIPAA Mistakes to Avoid!
by Derek Boczenowski on March 28, 2017 at 9:30 AM
Here at Compass, we have seen a huge upswing in the number of HIPAA / HITECH risk assessments we have been conducting over the last year. Covered entities (Doctors, Hospitals, Pharmacies) and health plans are obviously storing PHI (protected health information) and ePHI (electronic pr …
Why You Need an Incident Response Plan....Now!
by TJ Quirk on March 21, 2017 at 10:00 AM
You’ve been breached. Now what? New vulnerabilities are coming fast and furious. The unfortunate truth for most of us is, it’s not a matter of IF we are breached, it’s a matter of WHEN we are breached. Replace the worry with a plan - an Incident Response Plan. What qualifies as an inc …
IT Audit: Because you know I'm all about that Scope, 'bout that scope.
by Jerry Hughes on March 20, 2017 at 10:00 AM
The term IT Audit is so often used and misused by IT and business professionals in all industries. According to Wikipedia, IT Audit is defined as, “an examination of the management controls within an Information technology (IT) infrastructure. The evaluation of obtained evidence deter …
What is Social Engineering? Part I
by Derek Morris on March 14, 2017 at 9:45 AM
This post will be the first part in a series of three blog posts that outlines some of the most common methods “hackers” use, from a very high level, to gain access to your systems though social engineering tactics. The next two posts will dig a bit deeper into the different methods, …
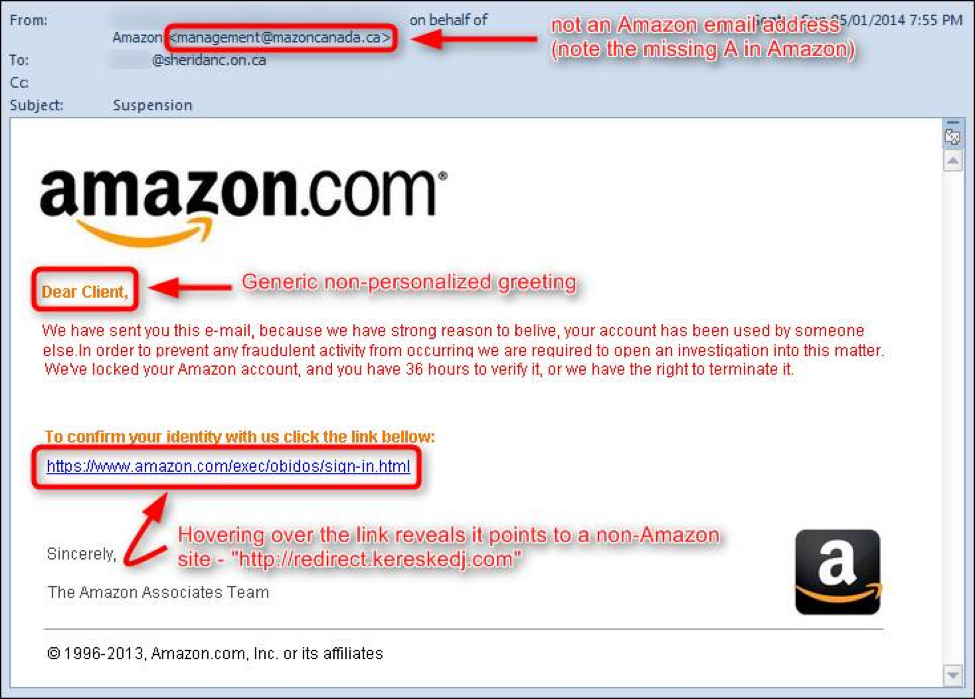
Phishing Examples - Protect Yourself From Ransomware
by Geoff Yeagley on March 8, 2017 at 10:38 AM
Fact: Phishing is the number one strategy that bad actors use to deliver malware to your organization. Fact: Phishing attacks come in a few different forms, known as phishing attacks and spear-phishing attacks. Fact: Ransomware is the most prevalent and dangerous form of Malware out t …
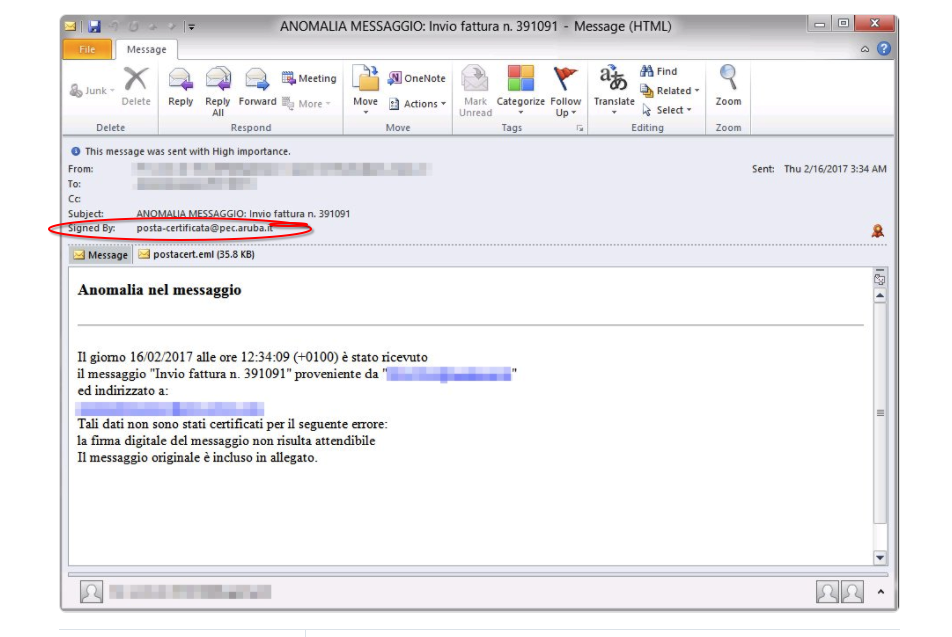
Phishing Examples: Grizzly Steppe and What You Need To Know
by Amy Johnson on March 1, 2017 at 10:00 AM
Within the past few years, Russian hacking has become a major issue in the United States. Not only has Russian Intelligence targeted political campaigns, they have also taken interest in other types of organizations who hold critical information. The Russians have developed a method o …
.webp?width=2169&height=526&name=Compass%20regular%20transparent%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)



.png)