Shipbuilders Council of America Spring Membership Meeting Takeaways
by Chanci Gadbois on May 30, 2025 at 12:50 PM
Earlier this month, I had the opportunity to attend the Shipbuilders Council of America (SCA) Spring Membership Meeting in Washington, D.C. The room was filled with national security leaders, lawmakers, and key players from across the U.S. shipbuilding ecosystem. What united everyone? …
Your SOC 2 Audit Is Complete – What Comes Next?
by Jerry Hughes on May 28, 2025 at 4:03 PM
Congratulations on achieving SOC 2 compliance! At Compass, we understand the effort it takes to meet the rigorous Trust Services Criteria and successfully navigate the audit process. Securing your SOC 2 attestation is a significant milestone, demonstrating your organization’s commitme …
10 Common Myths About SOC 2 Audits Debunked
by Jerry Hughes on May 28, 2025 at 4:01 PM
SOC 2 audits play a pivotal role in helping businesses showcase their dedication to safeguarding data and building trust with customers, partners, and stakeholders. However, misconceptions about the process often give rise to confusion, unwarranted stress, and inefficiencies that can …
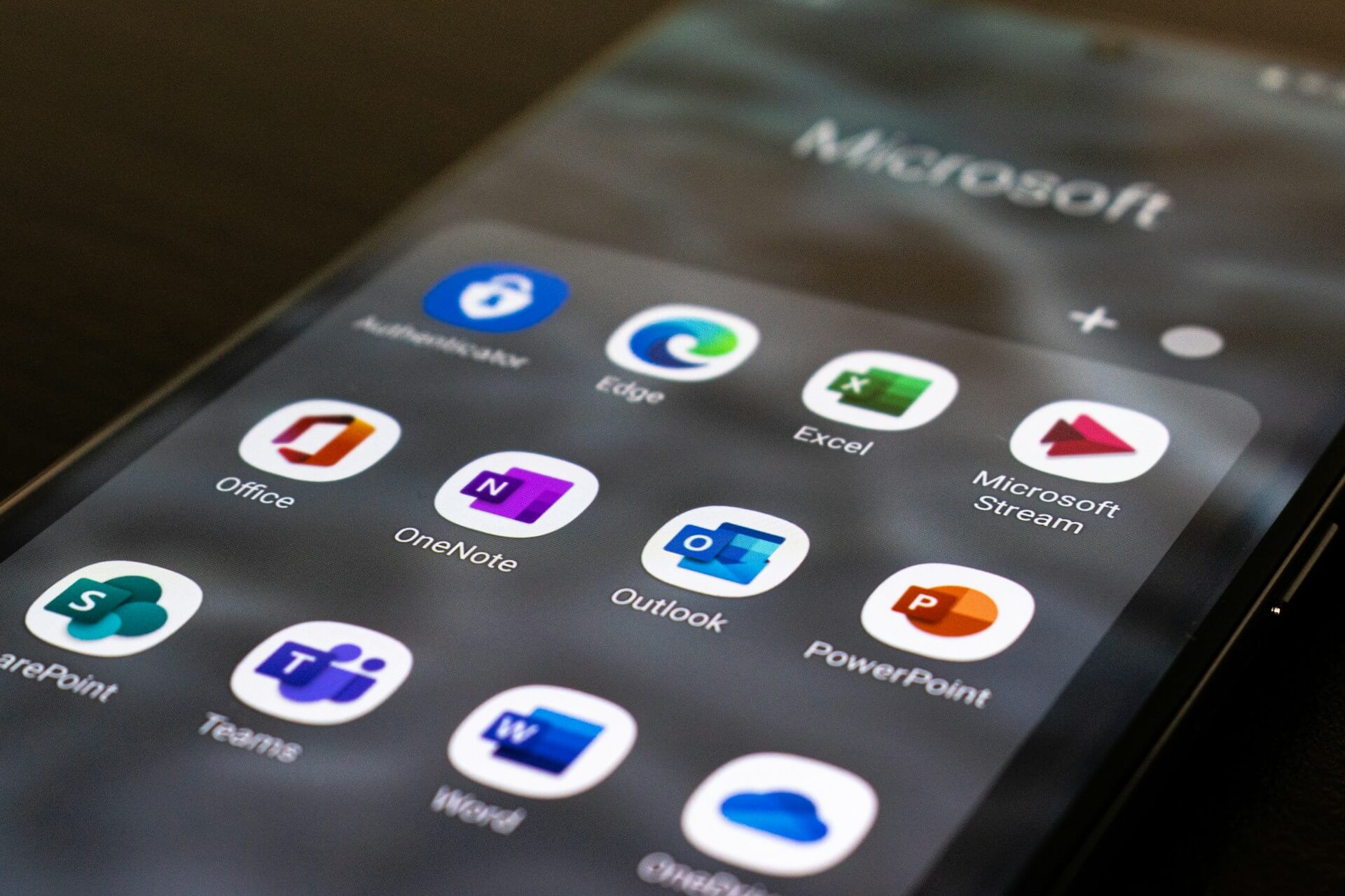
The Hidden Risks of User-Installed Apps in Microsoft 365
by Jesse Roberts on May 23, 2025 at 11:09 AM
The Microsoft 365 platform offers unparalleled flexibility, enabling users to collaborate, share, and automate workflows through an expansive catalog of third-party and custom-developed applications. But that convenience comes with a cost.
Misconfigured Microsoft 365: A Growing Threat Surface
by Jesse Roberts on May 15, 2025 at 1:49 PM
Microsoft 365 has become the backbone of modern business productivity. From Exchange Online and Teams to SharePoint, Power Apps, and Power Pages, its integrated services allow organizations to collaborate at scale. But with convenience comes complexity—and with complexity, misconfigur …
Is Your Internal Pen Test Just a Glorified Vulnerability Scan?
by Jesse Roberts on May 14, 2025 at 12:04 PM
Organizations today face an increasing number of internal threats—whether from malicious insiders, compromised credentials, or vulnerable systems exposed on the internal network. That’s why internal penetration testing has become a critical part of any mature cybersecurity program. Bu …
Why One-Size-Fits-All vCISO Security Programs Fall Short
by CJ Hurd on May 9, 2025 at 3:17 PM
When people talk about virtual Chief Information Security Officer (vCISO) services, they tend to focus on access: access to strategic guidance, access to frameworks, access to a security expert at a fraction of the cost of a full-time executive. And those benefits are real. But what d …
What Makes an Industry-Leading Cyber Insurance Policy Today?
by Kelly O’Brien on May 7, 2025 at 11:28 AM
Cyber insurance is no longer a niche product or an optional safeguard—it has become a critical pillar of enterprise risk management. As cyberattacks grow more sophisticated and regulatory pressures tighten, organizations of all sizes are reevaluating what they expect from their cyber …
CMMC & the Executive Order: A New Era for Shipbuilders
by William DePalma on May 2, 2025 at 2:23 PM
America’s shipbuilding renaissance is underway. On April 9, 2025, President Trump signed a sweeping executive order aimed at revitalizing the U.S. shipbuilding industrial base—an industry long seen as vital to both economic strength and national defense. At the same time, shipbuilders …
.webp?width=2169&height=526&name=Compass%20regular%20transparent%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)