What is Social Engineering? Part I
by Derek Morris on March 14, 2017 at 9:45 AM
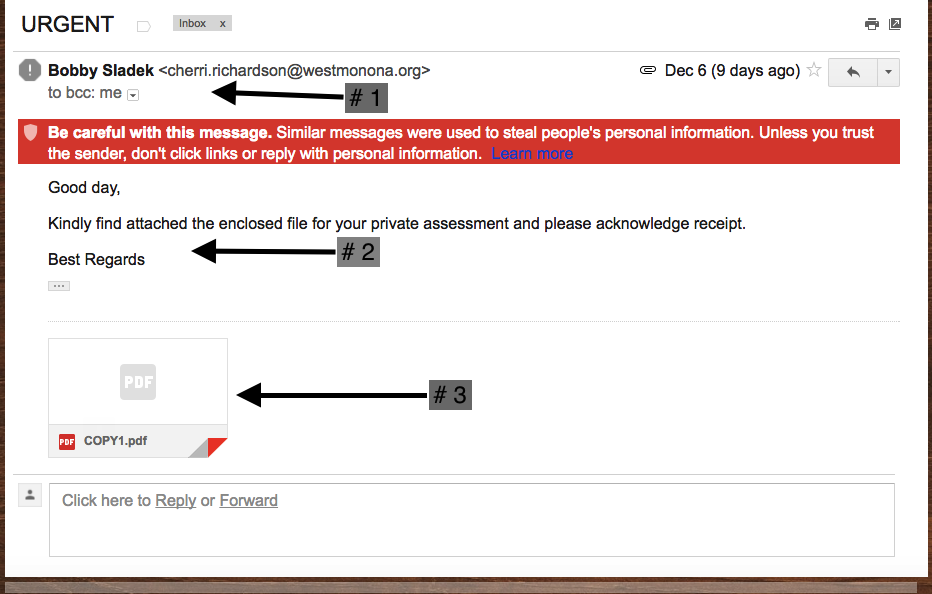
This post will be the first part in a series of three blog posts that outlines some of the most common methods “hackers” use, from a very high level, to gain access to your systems though social engineering tactics. The next two posts will dig a bit deeper into the different methods, …
Social Engineering Techniques and How Yahoo Put Us All At Risk
by Geoff Yeagley on December 15, 2016 at 1:49 PM
I read this article the other day that one of my colleagues passed on to me that said 91% of all cyber-attacks begin with a phishing email. That is an incredible number and one that should grab your attention and the attention of your Sr. Leadership team. As you dig further into the s …
Phishing - Even the Security Folks get Targeted Part II
by Geoff Yeagley on April 7, 2016 at 9:30 AM
Phishing schemes come in all different forms, shapes, and sizes. Hackers and thieves are smart and they will do whatever they think they can do to get access to your sensitive information. Some of these methods include emails, social media "like farming", pre-text calling, etc. The co …
How Phishing Emails Can Cost You $40,000
by Geoff Yeagley on March 22, 2016 at 10:00 AM
To me, math is what makes the world work. If you think about it, just about everything involves math, especially when it comes to business. When I was going through my MBA program, I really underestimated the amount of math and calculations that you needed to perform for essentially e …
Social Engineering - What You Need to Know
by Geoff Yeagley on January 19, 2016 at 11:04 AM
For those of us in the Information Security world, we hear terms thrown around all the time that are often interchanged, confused, and sometimes misused. One of those terms is Social Engineering. On the surface, this is a confusing term that doesn't appear to have anything to do with …
Social Engineering - Mitigating Your Risk
by Geoff Yeagley on January 12, 2016 at 11:41 AM
As we look into 2016 and what trends are going to take place this year in the world of Information Security, there is one thing that we can predict with significant confidence: Employees will remain the biggest threat to your Information Security Program and ultimately the safety of t …
.webp?width=2169&height=526&name=Compass%20regular%20transparent%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)