The NIST Cybersecurity Framework - The Protect Function
by Geoff Yeagley on July 19, 2017 at 10:43 AM
For the second part of our series on the NIST Cybersecurity Framework, we are going to be discussing the Protect function. Last time we discussed the Identify function which talked about the need to really understand your critical infrastructure, your systems, and the risks associated …
Another Day, Another Major Ransomware Outbreak...
by Geoff Yeagley on June 28, 2017 at 5:00 PM
A little over a month ago, a strain of Ransomware called WannaCry made headlines due to the incredibly successful nature of the attack as it infected hundreds of thousands of users around the world. This ransomware was delivered through an unpatched vulnerability in the Microsoft Oper …
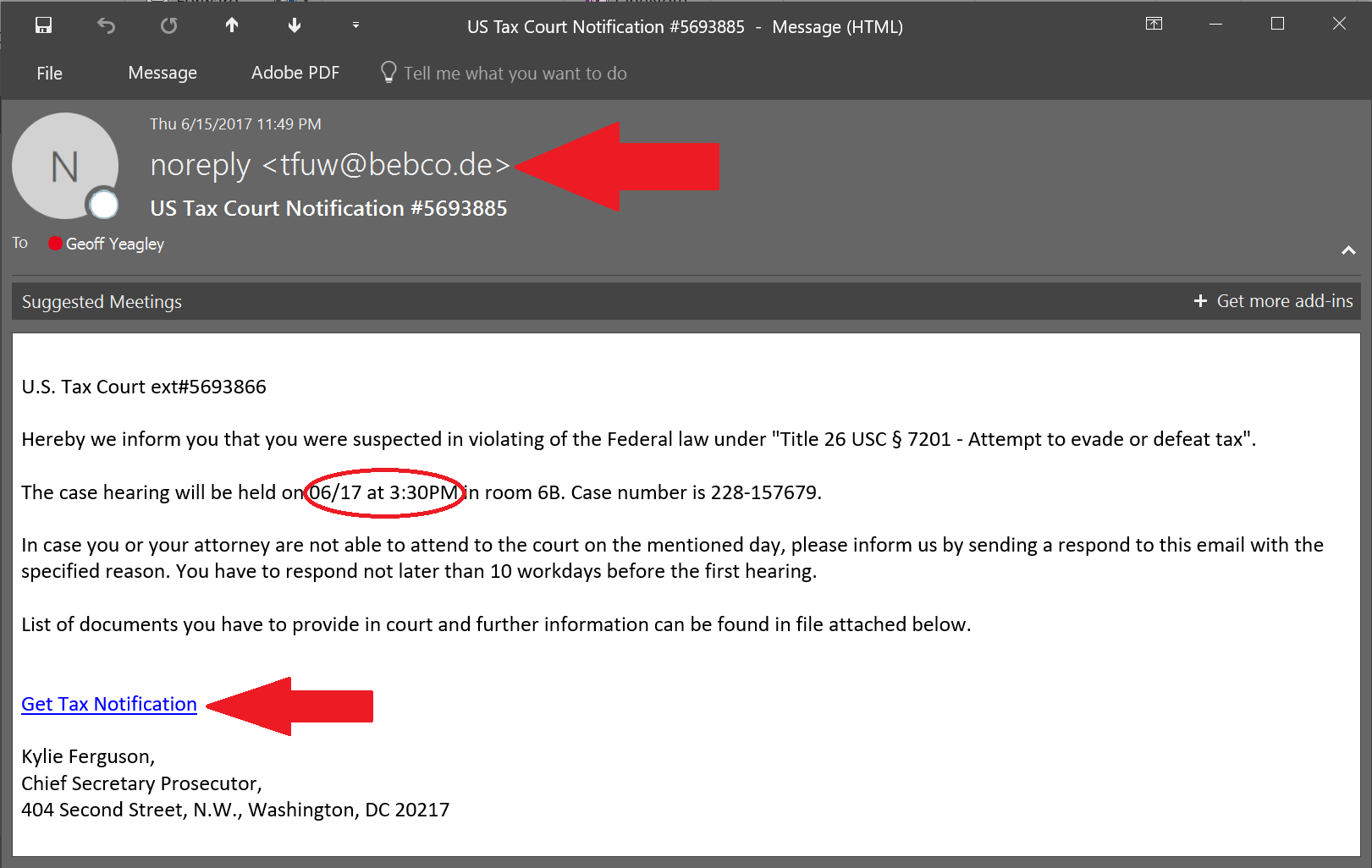
Phishing Examples: Even the Security Folks Get Targeted... Again!
by Geoff Yeagley on June 23, 2017 at 10:51 AM
If you have been reading the blog for a while, you know that I take phishing examples that I receive or my co-workers receive, post them to the blog, and point out the things that you need to be careful of. I do this primarily to educate folks about what the latest threats look like, …
The NIST Cybersecurity Framework - The Identify Function
by Geoff Yeagley on June 21, 2017 at 10:19 AM
Last week we provided a very high-level overview of the NIST Cybersecurity Framework, the core (5 functions) of the framework, and the categories within each function.
What is the NIST Cybersecurity Framework?
by Geoff Yeagley on June 15, 2017 at 11:33 AM
One of the most common questions that we get here at Compass is “What is an IT Security Framework?” This is a great question as folks sometimes confuse the various frameworks with different compliance requirements or regulations that they must adhere to based on their business. If you …
What is PII? Important Distinctions in Information Security
by Sarina Resnick on June 12, 2017 at 11:00 AM
What Is PII? PII is the acronym that keeps getting thrown around but never seems fully understood. It stands for "Personally Identifiable Information." Knowing what it stands for is just as important as knowing why it is becoming increasingly important to the integrity of your cyberse …
.webp?width=2169&height=526&name=Compass%20regular%20transparent%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)