IT GRC - Let's Talk About Risk!
by Geoff Yeagley on July 28, 2016 at 10:18 AM
Earlier this week we discussed IT Governance, Risk, and Compliance (IT GRC) with a specific focus on IT Governance. To read more of that post, click here. Today we are going to focus on the second component of IT GRC, IT Risk. In keeping with consistency, Gartner defines IT Risk as "t …
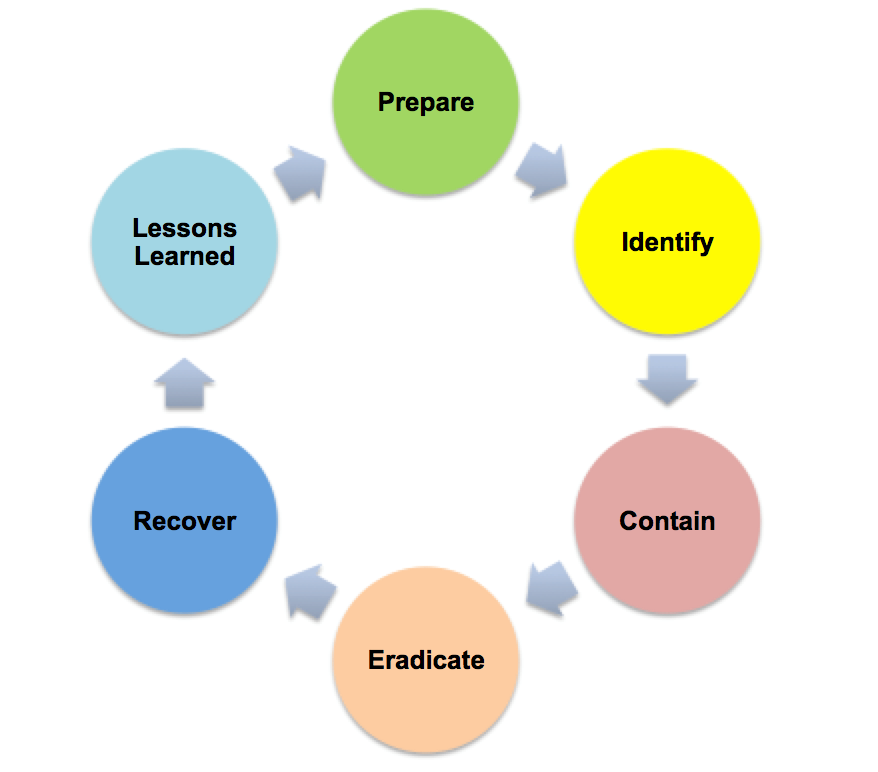
Critical Security Control 19: The Incident Response Plan
by Geoff Yeagley on May 17, 2016 at 12:16 PM
In the world of Information Security, we have all heard of the Center for Internet Security Top 20 Critical Security Controls (CSC's) which is formerly known as the SANS Top 20. This is a list of the 20 IT Security Controls that an organization can implement to strengthen their IT Sec …
The HIPAA Risk Assessment - Who Needs One and When?
by Geoff Yeagley on March 9, 2016 at 10:30 AM
Healthcare breaches are nothing new, in fact they have become quite common in the news on a weekly basis. As an example of this, a Central Florida Oncology provider recently announced that it suffered a data breach at the hands of a hacker, resulting in the compromise of the personal …
IT Risk Assessments and the SANS Top 20 - Part III
by Geoff Yeagley on February 16, 2016 at 10:56 AM
As we continue down our journey of discussing the importance of the SANS Top 20 Critical Security Controls, I want to make one important clarification that was brought to my attention by one of the readers of our blog. It should be noted that the controls that we are referring to in t …
IT Risk Assessments and the SANS Top 20
by Geoff Yeagley on January 26, 2016 at 10:14 AM
No matter what industry you are in, conducting a thorough IT Risk Assessment is critical to your organization for a number of reasons. First, it gives you a point in time measurement of how your IT Security posture compares to either various regulations or IT Security Frameworks.
Social Engineering - Mitigating Your Risk
by Geoff Yeagley on January 12, 2016 at 11:41 AM
As we look into 2016 and what trends are going to take place this year in the world of Information Security, there is one thing that we can predict with significant confidence: Employees will remain the biggest threat to your Information Security Program and ultimately the safety of t …
.webp?width=2169&height=526&name=Compass%20regular%20transparent%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)