Phishing Examples: Google Docs Scam
by Josh McDonald on May 4, 2017 at 2:16 PM
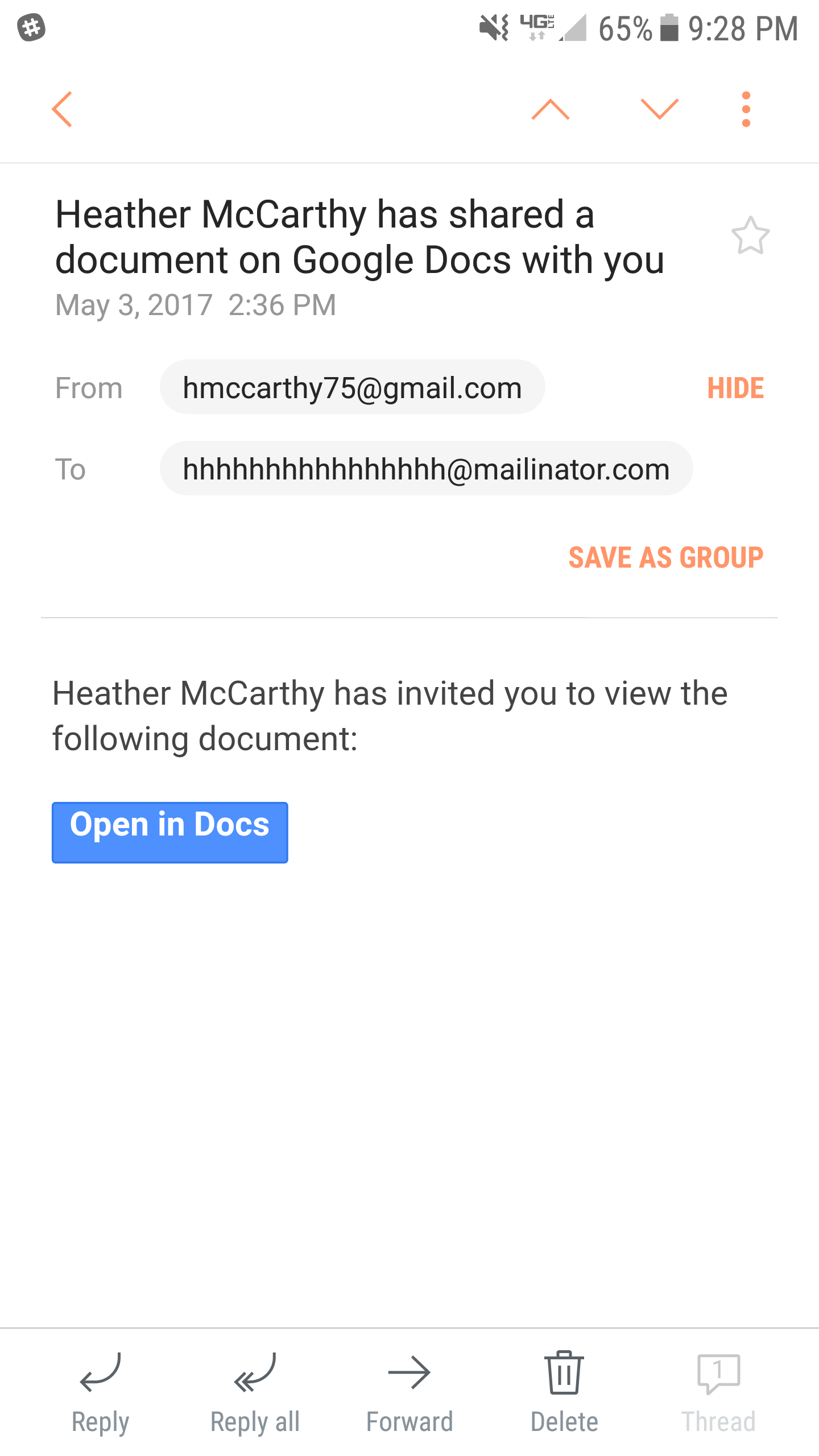
Friends of Compass, On this blog, phishing examples are nothing new. But, it is our job to share this information with you so that you stay alert, know what the threats are, and what you can do in the event you fall victim to an attack. You may have seen the recent reports of a Phishi …
What is Social Engineering? The Phishing Email
by Derek Morris on April 4, 2017 at 9:30 AM
What is Social Engineering? Part 2 The seemingly most common way for an attacker to use social engineering to gain entry, exfiltrate information or disrupt business is through email phishing. As I mentioned in the previous blog, slick tactics like using nicknames and shockingly proper …
Phishing Examples - Protect Yourself From Ransomware
by Geoff Yeagley on March 8, 2017 at 10:38 AM
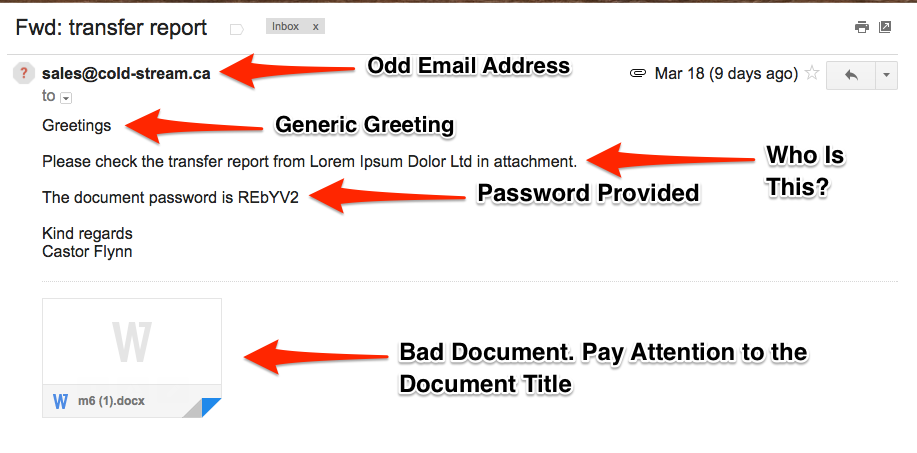
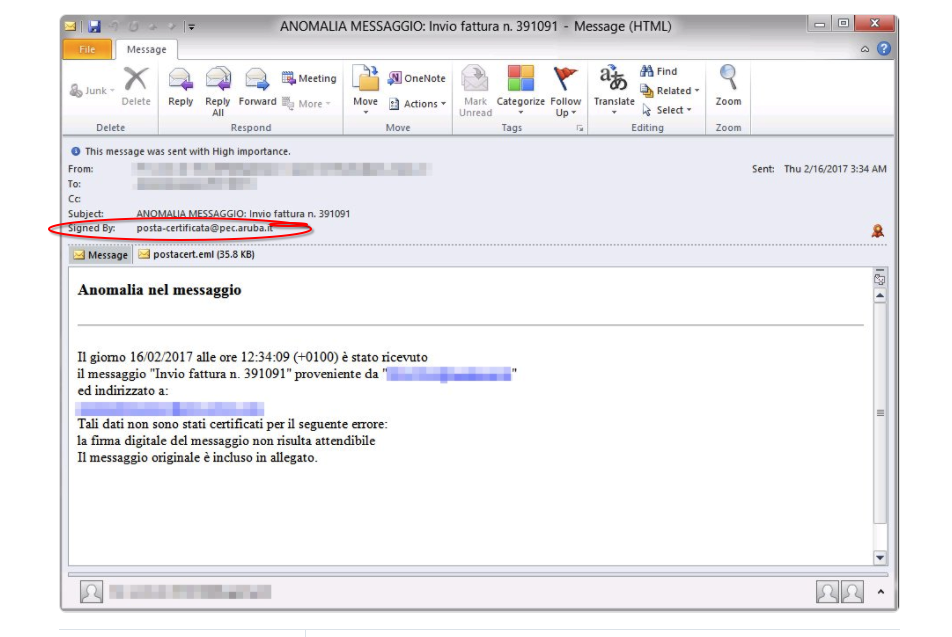
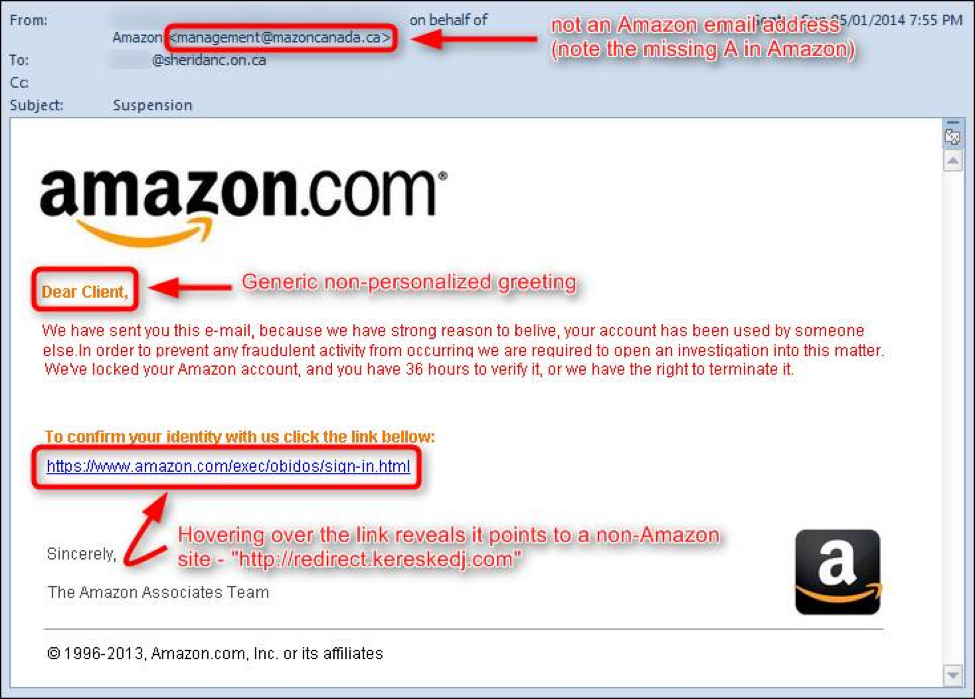
Fact: Phishing is the number one strategy that bad actors use to deliver malware to your organization. Fact: Phishing attacks come in a few different forms, known as phishing attacks and spear-phishing attacks. Fact: Ransomware is the most prevalent and dangerous form of Malware out t …
Phishing Examples: Grizzly Steppe and What You Need To Know
by Amy Johnson on March 1, 2017 at 10:00 AM
Within the past few years, Russian hacking has become a major issue in the United States. Not only has Russian Intelligence targeted political campaigns, they have also taken interest in other types of organizations who hold critical information. The Russians have developed a method o …
From Brute Force to the Phishing Email: How Hacking Has Changed
by Geoff Yeagley on September 15, 2016 at 2:35 PM
Hacking has changed. Both in how they do it and why they do it. Before, it was individuals trying to use brute force to gain entry into your network. It was aggressive and LOUD. Think of the idea of using a missile to swat a mosquito, same thing. Most of the time it was to prove a poi …
What is Phishing? Attack Techniques & Examples
by Geoff Yeagley on August 17, 2016 at 9:38 AM
Ransomware has dominated the news recently when it comes to IT Security. In fact, it was recently reported that 1 out of 5 companies that suffers a Ransomware attack ends up going out of business at least temporarily and 30% of affected companies lost revenue. Now we turn to the quest …
.webp?width=2169&height=526&name=Compass%20regular%20transparent%20website%20(1).webp)
-1.webp?width=2169&height=620&name=Compass%20regular%20transparent%20website%20smaller%20(1)-1.webp)